Proactive Measures for Protecting Your Sender Reputation

To keep their computers, accounts, websites, and mailboxes safe and secure, Internet users apply firewalls, antivirus tools, and anti-spam filters. Companies selling goods online and running online services, use anti-fraud systems to prevent fraudulent orders, account creations, abuse, and misuse of their infrastructure.
In recent years, the issue of security in the computer space has become more relevant than ever. With the emergence of artificial intelligence, attackers are increasingly improving their methods, endangering both businesses and individuals. The risks of artificial intelligence to cybersecurity are expected to grow rapidly as AI technologies become cheaper and more accessible.
People are increasingly falling victim to phishing, vishing, and smishing, which is the most common type of cybercrime. The worst thing is that you may become a victim of cybercrime without even knowing it. This is the email spoofing case – when your website domain or email domain is used by spammers to send spam and phishing emails.
What is Email Spoofing?
Email spoofing is a technique used by spammers to trick email recipients making them think the message came from an organization or person they know. The sender forges the sender’s email address which a recipient sees in the email client. If it’s a name and email address they recognize, they’re more likely to trust it.
Email spoofing is possible because outgoing email servers cannot verify whether the sender’s email address is legitimate or spoofed. Receiving servers and antimalware tools can help detect and filter spoofed messages, but not all email services have email authentication protocols in place.
Recipients can review the email headers of every message to determine whether the sender’s address is forged or not, but no one does it in reality, which plays into the hands of bad guys. People are used to trusting what they see in front of their eyes. So they open emails, download malware attachments, click malicious links, send personal data, and even wire funds.
Learn More: Email Spoofing Attacks
How Does Email Spoofing Hurt Sender Reputation?
While some people fall for the bait of phishing emails, others consider them to be spam and send a complaint showing ISP that messages sent from your domain are not wanted. User complaints are one of the major factors that ISP look at when calculating sender reputation. The more complaints, the lower sender reputation, and the more legitimate messages go to Spam.
The worst consequence of email spoofing attacks is blocked messages. When an email service provider sees an excessive number of user complaints or when your sender reputation becomes bad, it starts blocking emails from your domain. The inability to deliver important messages to the Inbox of your email subscribers leads to financial and reputational losses.
How to Protect Your Domain from Spoofing
The good news is that technologies don’t stand still and, at present, domain owners can use email authentication mechanisms to avoid or mitigate damage produced by email spoofing attacks. These mechanisms are:
– SPF (Sender Policy Framework). It works by requiring a domain owner to add a TXT record to DNS that names the IP addresses authorized to send emails from a given domain. The receiving server checks the SPF record to validate the email sender. By itself, SPF is not a perfect protection mechanism as failures can happen due to human mistakes and DNS issues.
– DKIM (Domain Key Identified Mail). This method also works by adding a TXT record to DNS. DKIM uses a pair of cryptographic keys to sign an outgoing message and validate an incoming message to make sure that the message wasn’t altered in transit. The weak side of this email authentication method is that the message can be forwarded without breaking the validity of the DKIM signature. This technique is referred to as a “replay attack”.
– DMARC (Domain-Based Message Authentication, Reporting, and Conformance). This method ties the two methods mentioned above and gives the highest level of protection when set to enforcement. DMARC is applied by adding a DMARC TXT record to a domain’s DNS. If an email receiver sees that a message passed DMARC authentication, it delivers it to the target recipient. When a message doesn’t pass DMARC authentication, the email receiver looks at the policy in the DMARC record to know what to do with the message.
Read: Email Authentication: the Ultimate Guide
Benefits of DMARC Authentication
Not only does DMARC prove the authenticity of an email message, but it also gives more advantages to senders who apply it:
- Visibility. You can include the email addresses in a DMARC record and receive reports from ISP. The DMARC reports have information about sources/IP addresses sending from a given domain and about SPF and DKIM passes and failures. Analyzing the reports, you can understand if anyone is using your domain on the sly and find out the breaches in your email authentication.
- Control. DMARC gives you the option to instruct the receiver what action to take when an email fails authentication. It’s done by adding the policy (p=) tag to a DMARC record. The p=none policy is normally used for collecting DMARC reports for analysis. The p=quarantine policy tells the email receiver to send the message to the Junk folder, and the p=reject policy tells to block the email at a mailbox gateway. You can also use the percentage tag (pct=) to apply the policy to a part of received messages. For example, pct=50 will tell the receiver to apply the policy to 50% of messages failing DMARC. The 100% reject policy will block all emails sent during a phishing attack and help you avoid user complaints and a damaged sender reputation.
- BIMI. DMARC makes it possible for email senders to apply the BIMI method which stands for Brand Indicators for Message Identification. This standard is in the adoption stage right now. Like other email authentication mechanisms, it will work by adding a TXT record to DNS. BIMI will allow email senders to show their logos next to their messages in the email clients. BIMI will work for the senders who use the ‘quarantine’ or ‘reject’ DMARC policy. Thus, if the logo appears, the recipient can trust the sender and safely open the message.
With that said, DMARC enforcement is the most reliable method of protecting a domain and brand reputation.
However, despite all the benefits DMARC provides, a lot of senders don’t use it to its full potential.
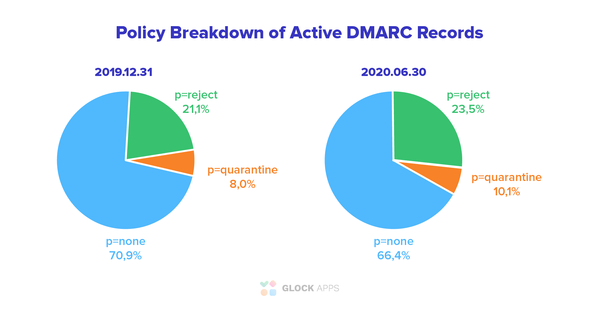
We think about two reasons that keep senders from applying DMARC enforcement:
- they are concerned about important messages that will be blocked if DMARC fails. To minimize the risk, it is recommended to set DMARC enforcement when 99-100% of legitimate messages pass DMARC authentication.
- they don’t have the human and time resources to analyze DMARC reports to understand whether or not the emails pass DMARC authentication. DMARC reports come in the format of XML files with aggregated data about emails sent from a domain. Depending on how often you send email campaigns and how many ISP your recipients are with, you may receive hundreds of XML files daily. It’s almost impossible for a human to parse all of them and understand the data.
How to Automate Domain Monitoring
The good news is that today there are tools like GlockApps DMARC Analyzer that do the analysis of DMARC reports for you. The tool creates a DMARC record for your domain that you must add to the domain’s DNS. When the reports start coming, DMARC Analyzer parses them, extracts the data, and presents it in a user-friendly format.
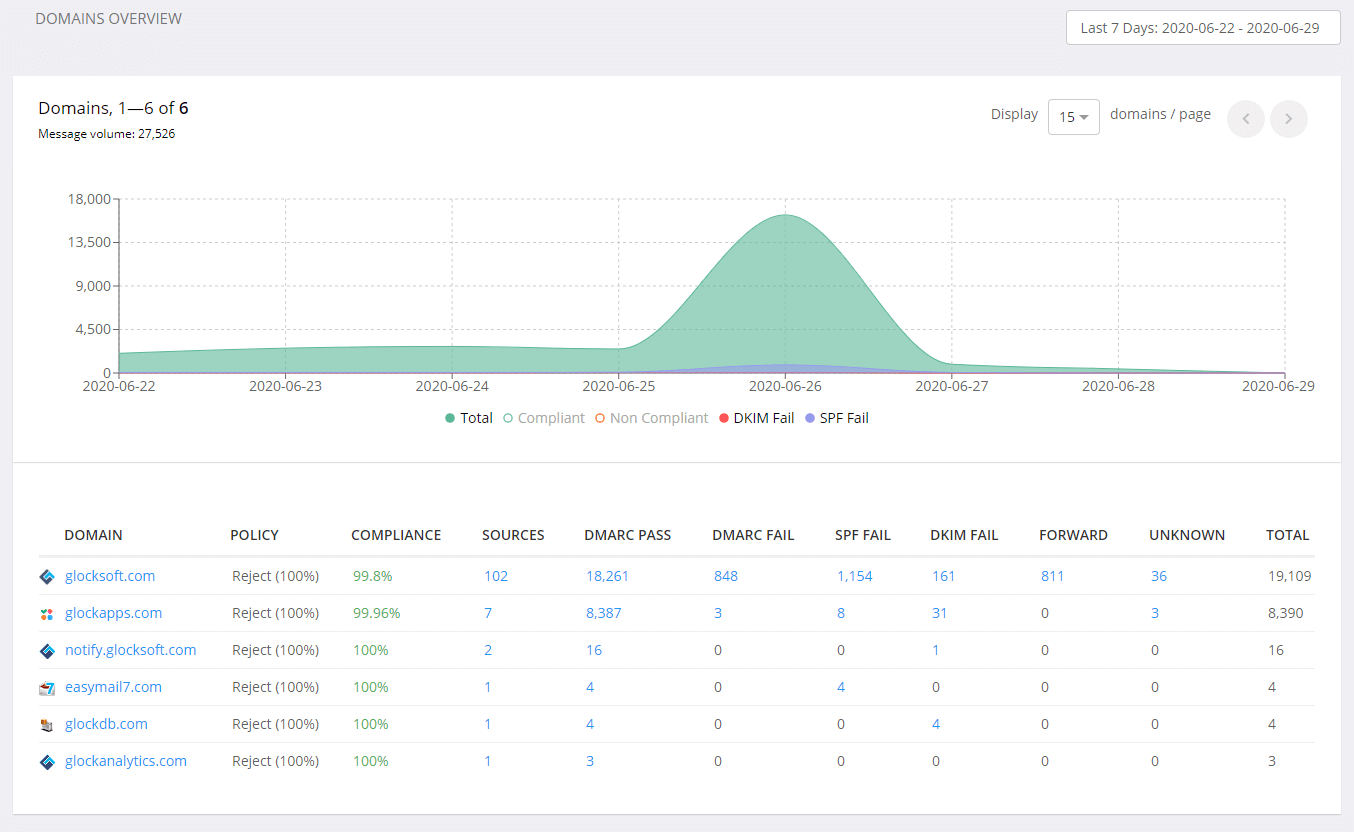
Example of aggregate reports in Glock DMARC Analytics
What you can learn from received data is:
- who is sending on behalf of your domain (authorized and not authorized sources);
- if your domain was subject to spoofing and sending spam;
- if the domain has valid SPF and DKIM records;
- if the messages sent by authorized sources pass SPF, DKIM, and DMARC authentication.
After you finish the monitoring stage, which takes around 1-2 weeks, and make sure that you send authenticated messages, you can move towards DMARC enforcement and change the policy to p=quarantine.
Read: 3 Steps to DMARC Enforcement
Email authentication can break at any time due to DNS issues or human mistakes. If you find it out in 24-48 hours, it can be too late because your important messages could have already been filtered out to Spam or blocked. To save yourself from such failed email campaigns, you can set up uptime monitors for SPF, DKIM, and DMARC records. The GlockApps Uptime Monitor verifies the DNS records 24/7 and detects the problems immediately after they occur.
You can set up alerts and the tool will send them to you via email, Slack, or Telegram in case of detected problems.
Automating domain monitoring with the right tool saves you days of manual work, eliminates human mistakes, and ensures that you are notified of any glitches instantly.
Takeaway
Email security is not a whim but a necessity. By applying email authentication mechanisms, not only do you protect your domain from email spoofing and keep the brand reputation intact, but you also take care of email users who might have been victims of email phishing attacks. With the right tools, you can automate your domain monitoring and make sure that you are alerted about any breaches on time before sender reputation is irreparably damaged.
You can create a free GlockApps account right now and get all the help with our support team, guides, and in-depth analytics.
With GlockApps free account, you’ll get:
- 2 email spam tests;
- DMARC reports for 10,000 DMARC capable messages;
- 14-day trial for uptime monitors (HTTP/TCP/TLS monitors, SPF/DKIM/DMARC monitors, and IP reputation monitors);
- instant notifications.



