How to Protect Your Sender Domain with DMARC: Using DMARC Enforcement

There is no other channel with such a wide audience reach than email. That is why legal business owners are using email to reach out to their clients and subscribers, and that is why spammers like to use email for malicious purposes. Hacking and phishing attacks in emails are increasing year by year.
The good thing is that there is a mechanism that allows email senders to protect their domains from misuse.
Why Deploy DMARC Record?
DMARC has been introduced to tie SPF and DKIM and to secure legitimate email senders and their recipients from email spoofing attacks.
DMARC stands for Domain-Based Message Authentication, Reporting, and Conformance. It is a mechanism of authenticating an email message to prove that it really comes from the sender it claims.
The DMARC authentication is done based on the two other methods SPF and DKIM and is implemented by adding a DMARC TXT record to a domain’s DNS.
Implementing DMARC record is a must-have for three main reasons:
- Email authentication.
- Domain protection.
- Email traffic visibility.
Read more: What is DMARC: Email Security with DMARC, SPF, and DKIM
What are DMARC Policies?
Not only does DMARC allow email senders to authenticate their emails, but it also allows instructing email receivers (AOL, Outlook, Yahoo! Mail, Gmail, and other Internet Service Providers) what to do with an email if it doesn’t pass a DMARC check. This way, you can tell the ISP to send an email pretending to be coming from you to the recipient’s spam folder or to block it at a gateway.
For this purpose, DMARC has three policies:
- None (p=none). This policy tells Internet Service Providers who adopted DMARC to do nothing with an email that failed the DMARC check. The email just goes to the Inbox or Spam folder of the receiver depending on how the ISP’s spam filters treat the email.
- Quarantine (p=quarantine). This policy tells Internet Service Providers to put emails that failed DMARC record in a special ‘quarantine’ folder – Junk or Spam.
- Reject (p=reject). This policy tells Internet Service Providers to reject all emails that failed the DMARC check. These emails will not land in any folder of the receiver.
In the DMARC record, you can also set a policy percentage. The percentage tag (pct=) instructs ISPs to only apply the DMARC policy to the specified percentage of the emails that fail the DMARC check.
For example, ‘pct=10’ will tell email receivers to apply the policy 10% of the time against emails that fail the DMARC check. The percentage works only for the ‘quarantine’ and ‘reject’ policies.
Example of a DMARC record with the ‘p=reject’ policy and pct=10:
v=DMARC1; p=reject; pct=10; rua=mailto:xxx@ar.glockapps.com; ruf=mailto:xxx@fr.glockapps.com; adkim=r; aspf=r; fo=0;
How to Create a DMARC Record?
Creating and adding a DMARC record is simple. There are tools like GlockApps DMARC Analyzer that allow you to quickly create a DMARC record. You add the DMARC record to your domain’s DNS and you are done. You send email messages from the domain and you receive DMARC reports.
GlockApps will parse each report and present the data about your email authentication in a comprehensive and user-friendly format.
Read more: How to Deploy DMARC Monitoring
Is It Necessary to Enforce the DMARC Policy to ‘Reject’?
After analyzing hundreds of DMARC reports collected by GlockApps, we found out that a lot of email senders successfully use a DMARC record but don’t advance to the stronger DMARC policy.
According to Socketlabs, 59% of senders don’t apply DMARC enforcement.
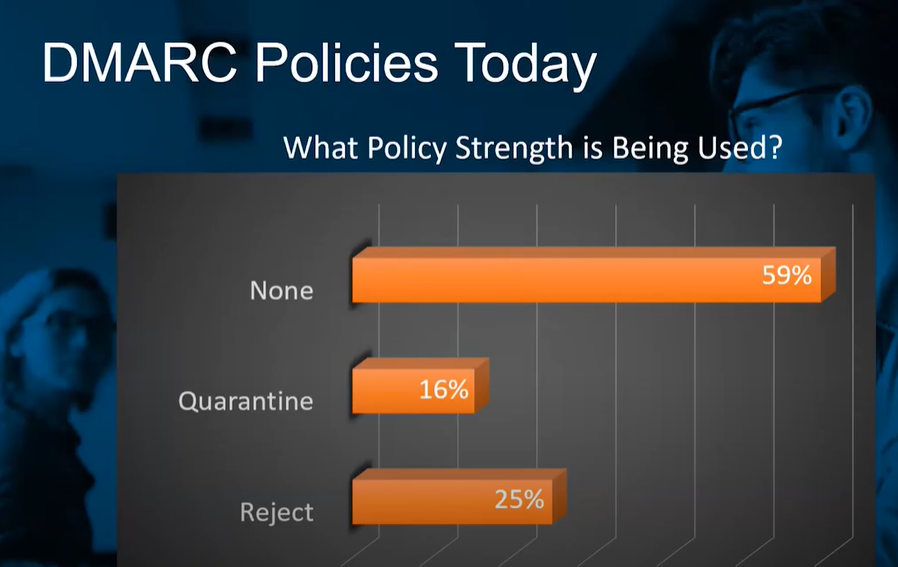
While the ‘p=none’ policy is good for a start when a sender is collecting data about their sending sources and email authentication, the goal every email sender should be focusing on is to move to the full protection level, e.g. the ‘p=reject’ policy.
However, the fears are understandable. No matter how well a sender authenticates their valid mail streams, it is nearly impossible to achieve a 100% DMARC compliance rate on all valid senders. It is often seen that a small percentage of all email messages coming from legitimate sources fail the DMARC checks. Such failures are caused by occasional DNS issues, message forwarding, or misconfigured SPF or DKIM records when a sender moves to a different email service provider.
With that said, 1 out of 10 000 legitimate emails will be rejected when the DMARC policy is enforced to the full rejection.
Despite this, at GlockApps, we believe that it is very important to have a domain fully protected against criminal attacks and accept the loss of some legitimate emails because of the DMARC ‘reject’ policy. The consequences of a phishing attack are much more detrimental for businesses than a tiny percentage of undelivered messages.
How to Enforce the DMARC ‘Reject’ Policy?
Switching from a ‘none’ policy immediately to a 100% ‘reject’ policy is discouraged. As we mentioned above, DMARC allows using a policy percentage to mitigate the impact of the policy.
It is recommended to enforce the policy in small steps and evaluate the impact of the enforced policy on deliverability. Since the enforcement will only apply to the specified percent of all sent emails, it will not lead to a huge loss of legitimate emails when the authentication is set up incorrectly.
We suggest the following scenario for DMARC deployment and enforcement:
1. Data Collection.
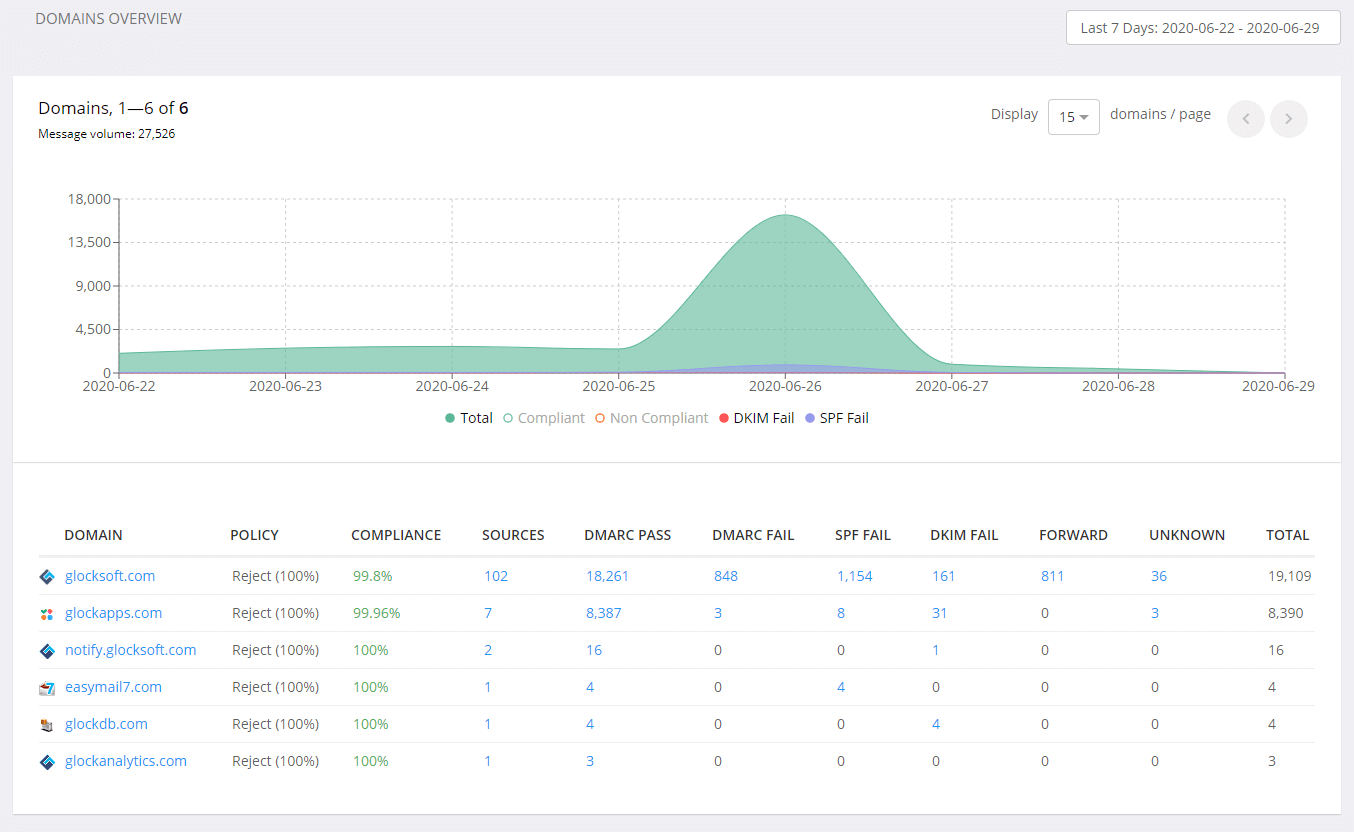
A DMARC deployment always starts with the DMARC policy set to ‘none’ which is the monitoring mode. After you publish a DMARC record with the ‘p=none’ policy, DMARC reports will start dripping in. In GlockApps DMARC Analytics, you will see the collected data under the Aggregate Reports dashboard.
Based on the collected data, you need to determine which steps are needed before you make progress.
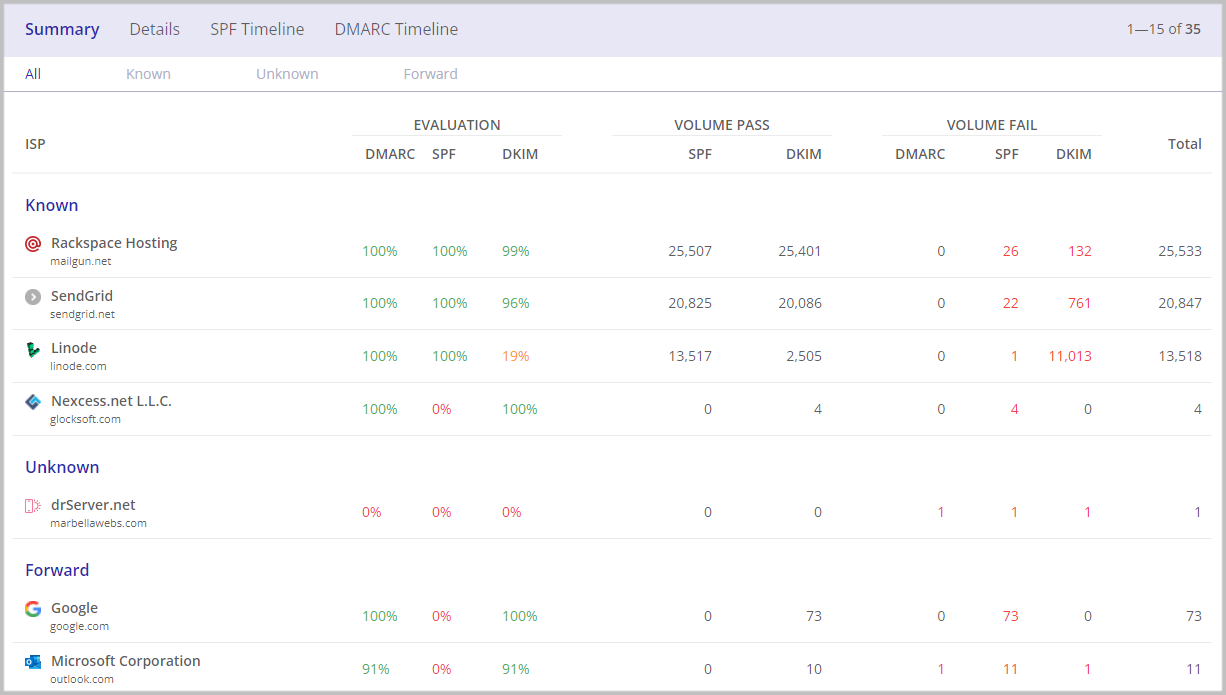
You can click on the ‘Sources’ number and determine if a mail source is valid or invalid for your company. Investigate the SPF, DKIM, and DMARC compliance rate for each legitimate (known) source and, if necessary, proceed with improving your SPF/DKIM records authentication to pass the DMARC check. This is needed to minimize the percentage of lost valid emails sent by legitimate sources, which may occur after a policy update.
GlockApps DMARC report: DMARC compliance by email sources
2. Safe Enforcement.
After achieving nearly 100% DMARC alignment for all legitimate email sources, you can move towards slow enforcement of the DMARC ‘quarantine’ policy. It’s recommended to do it in narrow steps of 5%, 10%, 25%, 50%, and 100% using the ‘pct=’ tag in the DMARC record.
After each change of the percentage, monitor the collected data about email authentication records for your authorized email sources for one or two weeks depending on how frequently you send emails to your subscribers.
In GlockApps, you can set up DMARC notifications that will be sent to you via email, Slack, or Telegram when the tool detects a drop in your SPF, DKIM, or DMARC compliance rate. Investigate and fix the cause of the drop before you can move to the next level of DMARC enforcement.
When you achieve the 100% ‘quarantine’, repeat the previous steps with the ‘p=reject’ DMARC policy. As soon as the 100% ‘reject’ policy has been applied, DMARC enforcement has been fully deployed and the domain is fully secured against phishing and spoofing attacks – all emails that fail the DMARC record check, are rejected.
GlockApps DMARC aggregate report
3. Ongoing Monitoring.
However, after you reached the 100% ‘reject’ policy, you are not yet done. It’s very important to constantly monitor all authentication data in your DMARC Analytics account. The use of new email service providers, IP addresses, and domains can give authentication issues and result in losing legitimate emails.
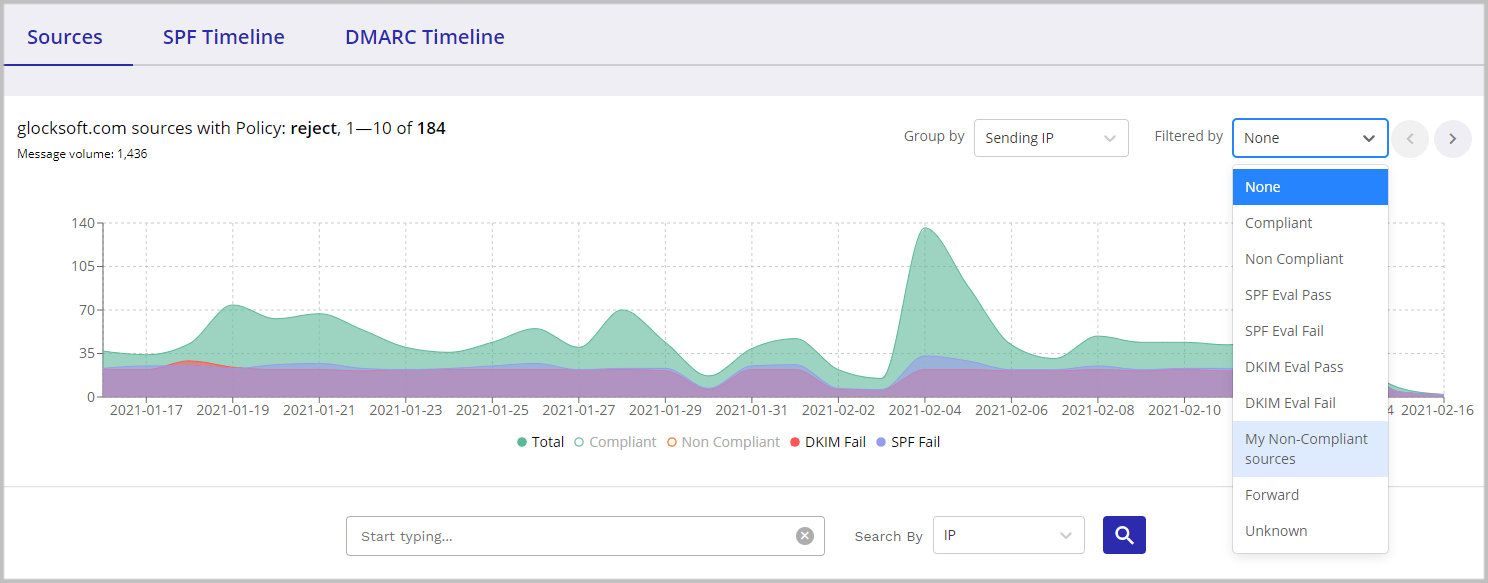
To quickly find out what valid sources send non-compliant emails, you can filter the data for the domain by “My Non-Compliant Sources.” GlockApps determines your authorized sources based on the senders included in the SPF record set up for your domain. If your legitimate sources are all DMARC compliant, you can filter the data by “Non-Compliant” and see who is sending non-compliant emails on behalf of your domain (new valid sender, malicious senders?).
GlockApps DMARC report: filter by DMARC non-compliant sources
Read more: How You Can Leverage the DMARC Analytics to Fix Deliverability Issues
Ongoing monitoring of the DMARC compliance rate helps discover authentication issues before they impact deliverability, determine new legitimate email sources, and sources sending unauthorized emails from your domain, e.g. spoofing and phishing attacks.
DMARC’s alignment with the ‘reject’ policy will work for your sender’s reputation and deliverability in the long term. No one will receive a phishing or scam email from you, no one will send a complaint. With DMARC enforcement, you eliminate three major factors that could ruin your deliverability: user complaints, emails filtered to Spam, and spam trap hits.
If you want to begin the process today – GlockApps is here for you.
You can start using DMARC Analytics right now with 10,000 free monthly DMARC messages
and unlimited domains. We provide all the help with our support team, guides, and in-depth analytics.
Learn More About DMARC:
DMARC Report Analyzer- Improve Email Deliverability
Why Every Business Needs DMARC
DMARC Adoption: What’s the Problem?