The Ultimate Guide to DMARC Reports
Learn Everything about DMARC and How to Read DMARC Reports

Email marketing is a booming industry. Therefore, it’s important to learn everything you can about DMARC reporting to ensure your emails reach your customers. DMARC or Domain-Based Message Authentication is a powerful tool that protects your brand from phishing and spoofing attacks.
But how do you set up DMARC? How do you analyze DMARC reports? And how will DMARC impact your email deliverability?
Our DMARC guide will walk you through everything you need to know about DMARC reporting, including:
- What is DMARC (Domain Based Message Authentication)?
- What is a DMARC Report?
- How to Read DMARC Reports
- Why is DMARC Important?
- How does DMARC Work?
- How do I Publish a DMARC Record?
- What is DMARC Enforcement?
- DMARC Record Example
- What are DMARC Tags?
- How does DMARC affect Email Deliverability?
- DMARC Report Examples and Explanations
- Free DMARC Reporting Tools
- How to Use GlockApps DMARC Analyzer
What is DMARC?
DMARC (Domain-based Message Authentication Reporting and Conformance) is an email validation system that helps protect your email domain from being used to send phishing emails, scams, and other spam.
It is built upon two existing email authentication technologies that are used to associate a piece of email with a domain: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). DMARC reinforces email authentication created by SPF and DKIM and provides the strongest way of email domain protection.
Another good thing about DMARC is reporting. After you publish a DMARC record in your domain DNS, you will get the information about all the sources which are sending emails on behalf of your domain.
The information given by DMARC comes as feedback reports generated by organizations that process incoming emails. By analyzing these reports, you can identify all your email streams, determine illegal sources and make sure that all legal sources pass email authentication checks.
Note: Not all mail servers check DMARC before receiving a message. ESP’s must allow you to set a custom Return-Path domain in order to fully support DMARC.
Is Your DMARC Set Up Properly?
What is a DMARC Report?
DMARC reporting is a process that allows organizations to receive aggregate reports regarding the delivery of their emails. DMARC provides visibility into external sources, including ESPs and ISPs, allowing for enhanced security when it comes to email deliverability. There are three main types of reports: failure messages, success messages, and authentication results from SPF or DKIM.
Failure messages are sent when an email fails SPF or DKIM. This will include the original message headers that were received, additional header information from DMARC, and a list of identifiers that failed authentication.
Learn More about DMARC Fails: DMARC Fail: What Causes DMARC Failure?
Success messages provide aggregate data on emails verified using SPF or DKIM. They give insight into how your domain is being used for sending mail by revealing any unauthorized mail sources. Finally, authentication results detail which policies successfully authenticated against each identifier within the scope of the policy during the reporting period.
All reports contain valuable insight to help you improve security protocols surrounding email deliverability. Be sure to review our DMARC Report examples to learn more about the difference between aggregate reports and failure reports.
How are DMARC reports generated?
DMARC reports are generated by inbound mail servers as part of the DMARC validation process.
DMARC reports are usually sent once a day by email but can be changed based on your preferences. If you add the rua DMARC record tag to your DMARC record, you can audit them using email reports. They’re sent to the addresses you specified when creating your DMARC record. Every server that receives mail from your domain must send a report if reports are enabled with the rua DMARC record tag in your DMARC record.
A report is submitted for each message received after applying one or more DKIM signatures to an email, where at least one signature successfully authenticates with the sending IP address included in a designated DNS record (the “envelope”). If no valid DKIM signature can be applied to any given message, then there will not be a corresponding DMARC aggregate report. DMARC reporting happens when messages fail SPF check AND/OR similarly fails against SenderID Verify OR failed DKIM authentication.
DMARC aggregate reports include information about all messages that were not delivered because they didn’t pass either SPF or DKIM checks and also don’t have other problems.
How to Read DMARC Reports
DMARC reports will inform your email marketing team or your security team which messages sent from your domain are authenticated by SPF and DKIM. DMARC reporting also lets your teams regularly review who is sending mail from your domain and can alert you to potential spammers or unauthenticated sources.
After you set up DMARC, you will start receiving DMARC XML reports with your DMARC performance. It may be difficult to interpret and store these DMARC reports so we advise you to use a DMARC Report Analyzer to help you read DMARC Reports.
Try our DMARC Report Analyzer
Also Read: Free DMARC Report Analyzer: How to Read DMARC XML Reports
What’s the Difference between a DMARC Report and a DMARC Aggregate Report?
A DMARC aggregate report is a collection of regular DMARC reports. As with all authentication protocols, DMARC reports are best understood in aggregate rather than via individual sender. You can use our DMARC Analyzer to view 10,000 individual or aggregate reports monthly for free.
When viewing the DNS-based report produced at daily intervals, it’s easy to filter out false positives by looking only at the senders that have passed or failed authentication against your published policy. You may even want to blacklist certain domains using this information if their failure rate becomes too high. But keep in mind that doing so could impact legitimate email campaigns as well.
Why is DMARC Important?
Malicious emails remain a serious threat, making up approximately 46.8% of global email traffic last year. Additionally, 2.3% of these unwanted emails contain malicious content, highlighting the growing risks of phishing and malware attacks.
The financial impact of phishing is staggering. In 2024, Business Email Compromise (BEC) scams continued to pose significant threats to organizations worldwide. The FBI’s Internet Crime Complaint Center (IC3) reported that between October 2013 and December 2023, BEC incidents resulted in global losses totaling nearly $55.5 billion.
DMARC is an email authentication system created to help standardize the way companies communicate with customers. When implemented correctly, DMARC will ensure all messages sent from your organization’s domain are authentic and prevent impersonators from spoofing your company domain in order to gain access to information or financial accounts belonging to you or one of your employees.
DMARC was created by a group of security experts and email providers in an effort to stop email spoofing.
It has become more important in recent years as modern hackers use DMARC to make their scam emails appear legitimate by spoofing the same IP address used in regular business communications between two companies. Since many people tend to trust messages coming from a colleague’s or company’s real email address, they may easily fall for these scams without looking too closely at any warning signs such as poor grammar or spelling mistakes. With this high-risk behavior currently happening on a daily basis, it is crucial that businesses do everything they can to stay protected against scammers with DMARC compliance protocols.
Learn More: Why Every Business Needs DMARC
How does DMARC Work?
DMARC is dependent on your established SPF and DKIM. All three components work together to authenticate your email messages and determine what to do with them. DMARC also piggybacks on the well-established Domain Name System (DNS).
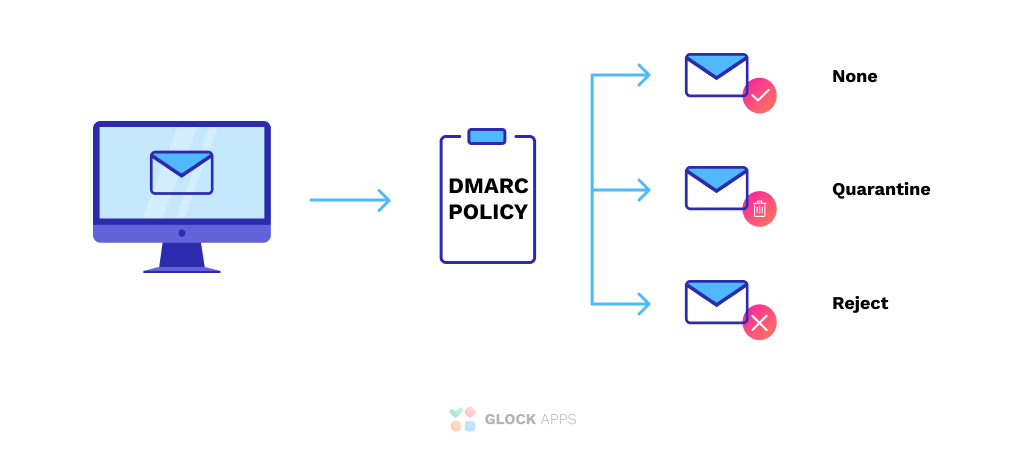
Essentially, a sender’s DMARC record instructs a recipient of the next steps (e.g., do nothing, quarantine the message, or reject it).
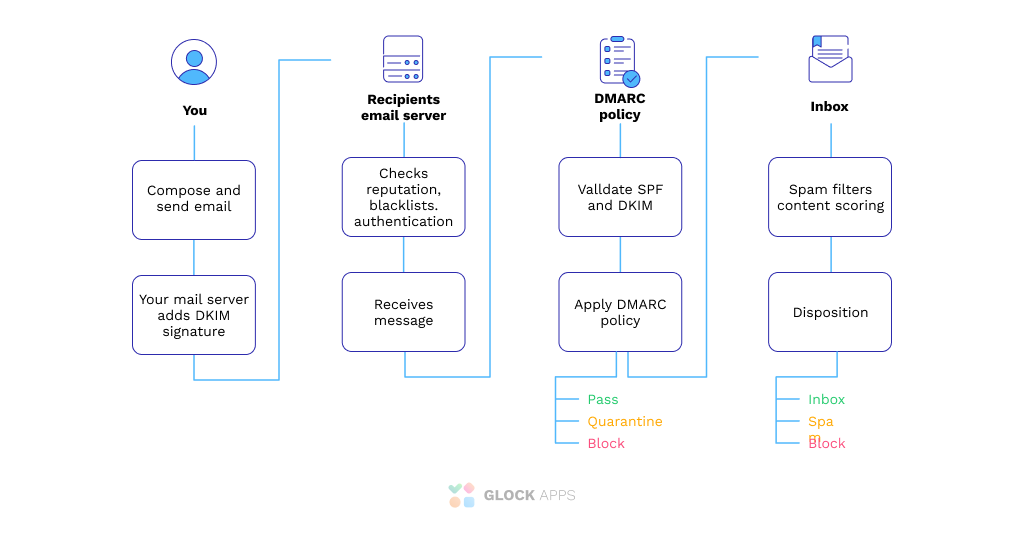
Here’s how DMARC works:
- You craft your email and hit send to your loyal contacts.
- Your mail server adds a DKIM header, which looks for forged sender addresses.
- DKIM confirms that you are legit.
- Your email heads on over to your recipients’ mail server.
- The recipients’ email server checks for valid SPF and DKIM mechanisms
- Your email will pass authentication or be quarantined or rejected depending on your DMARC policy.
- If passed, your message will be delivered to your recipient.
DMARC reporting is the first step to understanding your protected domain’s email health. It provides visibility into which sources are sending with spoofed domains and identifies unauthorized messages that pass SPF/DKIM validation but fail DMARC authorization checks. These reports can be viewed in aggregate or by the individual senders through a simple-to-use online dashboard. There are several well-known services such as our DMARC Analyzer that offer you 10,000 DMARC messages for free every month.
The next critical component of your journey toward improved email authentication security is aligning policies with business goals via DMARC aggregate report analysis. This vital step enables you to see trends within your DMARC.
How do I Publish a DMARC Record?
- Ensure every application/tool you use to send email is authenticated with both SPF & DKIM.
- Sign into your domain hosting provider.
- Go to the DNS settings for your domain.
- Create a TXT record with the following values:
- Name/Host/Alias: _dmarc
- TTL: 3600 or default
- Value/Answer/Destination: v=DMARC1; p=none; rua=mailto:dmarc@example.com
- Save the record.
What is DMARC Enforcement?
According to a new study, most businesses only complete the DMARC implementation stage and don’t proceed to enforcement. This can be a big mistake! Enforcement is an important component of DMARC, as merely putting in place DMARC in your organization isn’t enough to set up and combat fraudulent emails. DMARC’s major purpose is to allow domain owners to enforce their own DMARC policy for how they want receivers to respond to emails and messages that fail DMARC authentication.
DMARC enforcement at an organization allows the domain owner to specify how they want to handle an email that fails authentication, unlike SPF and DKIM.
With an enforcement policy, domain owners can tell receivers to put unauthenticated messages in the spam folder or reject them entirely. Once a message has been authenticated by one of these two reporting mechanisms if it’s still considered “unverified” DMARC reports are generated every 24 hours for seven days about each verified email that was sent with authentication data present and did not pass either SPF check. There are three kinds of aggregate reports: Policy (p) says what you want to be done with messages failing both tests:
- p=None policy provides zero enforcement and allows unauthorized emails that fail verification to land into the receiver’s inbox without any hindrance.
- p=Quarantine policy provides lodges emails that fail DMARC authentication into the spam folder of the receiver’s email server, thereby quarantining them.
- p=Reject policy deletes or discards unauthorized emails that fail authentication before they are delivered at all.
Learn more: The Ultimate Guide to Email Authentication
What does a DMARC Record Look Like?
Here is an example of DMARC record – this is SendGrid’s DMARC record:
v=DMARC1; p=reject; sp=reject; pct=100; adkim=r; aspf=r; rua=mailto:dmarc_agg@vali.email,mailto:dmarc_rua@sendgrid.com; ruf=mailto:dmarc@sendgrid.com; fo=1; rf=afrf; ri=86400
You can also use our GlockApps Domain Checker to view the SPF and DMARC record for any domain if they have one published.
What are DMARC Tags?
DMARC tags are made up of multiple tag-value pairs that are used to tell an email server how it should treat a particular email based on the sending domain’s DMARC record. Each tag-value pair has its own unique meaning, which together can provide more information about what actions need to be taken for each specific sender.
Required tags
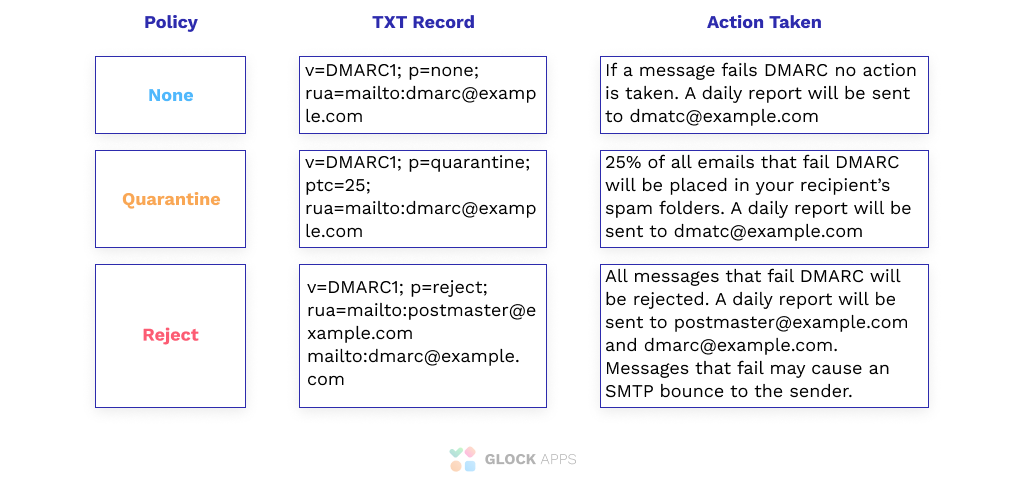
Version (“v”): Must take the value DMARC1 (e.g v=DMARC1). Otherwise, the entry will be ignored.
Policy (“p”): Policy for receiving messages. Determines the DMARC policy for receiving messages for the domain and subdomains.
- None (p=none): no action is required.
- Quarantine (p=quarantine): the domain possessor asks that failed DMARC messages are considered suspicious. Thus the messages will end up in the spam folder, be flagged as dubious.
- Reject (p=reject): owner is requesting that messages failed by DMARC verification be rejected. The rejection must be done during an SMTP transaction.
Optional tags
RUA Report Email Address (rua): Create separate email addresses for sending aggregated reports, separated by commas. It is possible to use mailto: links to submit reports by mail. This email is used to receive DMARC reports.
Learn More: What is a Rua tag and why does my DMARC record need it?
RUF Report Email Address (ruf): Create separate email addresses to submit failure reports, separated by commas. Specifying this tag implies that the owner requires recipient servers to send detailed reports on every message that fails DMARC validation. This email is used to receive failure reports.
Percentage (pct): It specifies the number of emails to be filtered, indicated as a percentage. For example, “pct = 20” will filter 20% of emails.
Subdomain Policy (sp): This tag represents the requested handling policy for subdomains.
ADKIM Tag (adkim): DKIM record authentication check. It can take the value Relaxed “r”, or Strict “s”. The default is “r”.
- In relaxed mode, if the DKIM record being verified belongs to the domain d=example.com, and the message is sent from email@news.example.com, the verification will pass.
- In the strict mode, the check will be passed only if the sending comes from an address on the example.com domain. Subdomains will not pass validation.
ASPF Tag (aspf): SPF record authentication check. By analogy with adkim, it can be Relaxed “r”, or Strict “s”. The default is Relaxed “r”.
How does DMARC affect Email Deliverability?
DMARC is more than just email security. It’s also about email deliverability. DMARC tells ISPs (like Gmail, Yahoo! Mail, and Outlook) how to handle your emails based on their level of authentication or spam score. In other words: it helps you improve your inbox placement so that legitimate mail reaches the intended recipient rather than being blocked as spam by ISP filters.
You can improve your email deliverability by:
- Publishing a DMARC record
- Using your DMARC reporting results to improve your authentication results
- Enforcing a DMARC policy
Setting up a DMARC Record with a reject policy will prevent spoofing by ensuring only authenticated emails are sent from your domain. This will help you maintain a positive domain reputation and sender score which leads to better email deliverability. Another benefit of enforcing DMARC with a reject policy is the ability to implement BIMI. BIMI is an additional layer of email authentication that displays your logo in your clients’ mailboxes. BIMI allows your email to stand out from the rest.
If you want to keep your emails out of spam it’s essential to implement SPF, DKIM, and DMARC as soon as possible.
DMARC Report Examples and Explanations
DMARC maintains 2 types of reports: aggregate reports and failure (forensic) reports. These 2 reports serve different purposes.
DMARC Aggregate Reports contain:
- Source of Sending IP Address
- When the email was sent
- Which domain or organization that sent the report
- SPF domain
- SPF domain alignment check: pass or fail
- SPF authentication result: none, neutral, pass, fail, softfail, temperror, or permerror
- DKIM domain
- DKIM domain alignment check: pass or fail
- DKIM authentication result: none, neutral, pass, fail, policy, temperror, permerror
- The policy applied by the receiver: None, Quarantine or Reject
DMARC Failure Reports (Forensic Reports) contain:
- Source of Sending IP Address
- From email address
- Recipient email address
- Email subject line
- SPF and DKIM Authentication results
- Received time
- Email Message headers which include the sending host, email message ID, DKIM Signature, and any other custom header information.
Free DMARC Reporting Tools
You can get 10,000 DMARC messages for FREE every month with our DMARC Analyzer. You must be the domain owner in order to publish a DMARC record and set your DMARC policy.
You can use our DMARC analyzer to:
- Publish a DMARC Record with your preferred DMARC policy
- Send DMARC Aggregate reports to GlockApps
- Review Sending IP Addresses
- Review SPF & DKIM Signature
- Review your DMARC reports.
- Review your published DMARC policy & record
How to Use GlockApps DMARC Analyzer
Step 1. Add Domain.
Login to your account with GlockApps.
Go to DMARC Analytics and click “Add Domain”.
Enter a domain and click “Next.”
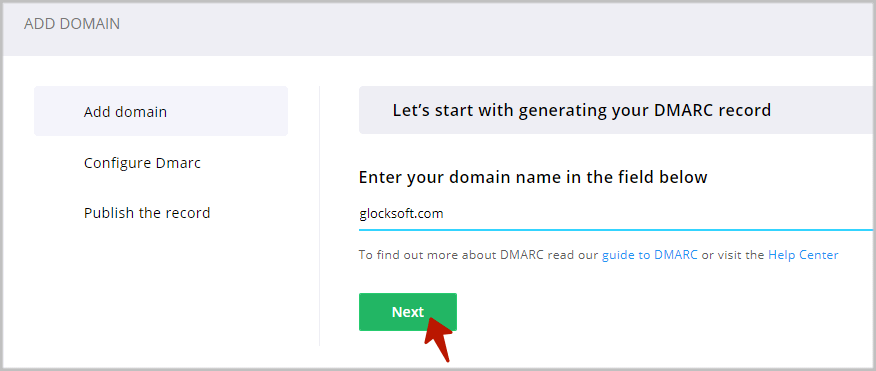
Step 2. Configure DMARC Record.
Now, you can select a DMARC policy for your domain and sub-domains, choose the alignment mode for your DKIM and SPF, and add more email addresses that will receive DMARC reports.
DMARC Policy
The DMARC policy tells the email receiver what to do when an email message fails DMARC authentication. The following policies are available:
None – No action is applied to an email if it fails the DMARC authentication. This is the monitoring mode that senders can use to collect information about their email sources. We recommend using the “none” policy if you are just starting with DMARC.
Quarantine – An email is sent to the Spam folder if it fails the DMARC authentication.
Reject – An email is rejected and is never delivered if it fails the DMARC authentication.
If you want to use a different policy for subdomains, choose “Yes” and select a policy different from the one you set for your domain.
Alignment Mode
Alignment forces the domains authenticated by SPF and DKIM to have a relationship to the “Header From” domain.
For a strict DKIM alignment, the domain in the ‘d=tag’ from the DKIM signature header has to match the domain used in the header “From” field. In the relaxed mode, only the organizational domain has to match.
For a strict SPF alignment, the domain used in the “Mail From” address (or Envelope From or Return-Path) has to match the domain used in the header “From” email address. In the relaxed mode, only the organizational domain has to match.
For example, yourdomain.com and email.yourdomain.com will align in the relaxed mode but fail in the strict mode. In the strict mode, domains have to match exactly.
DMARC passes based on SPF alignment or DKIM alignment or both. When SPF and DKIM alignment fails, DMARC fails too.
DMARC Reporting
The DMARC Analytics wizard will add the email addresses pointing to GlockApps (@ar.glockapps.com and @fr.glockapps.com) to the DMARC record.
Click “Next”.
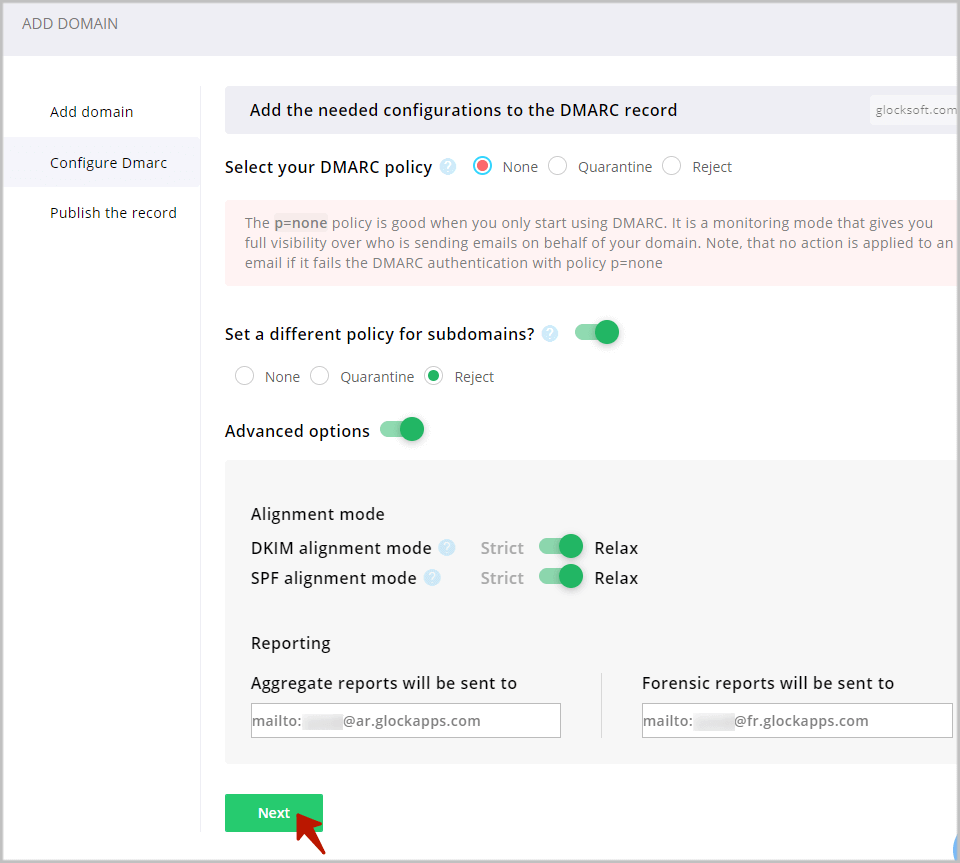
Step 3. Publish a DMARC Record in DNS.
To finish, you must add or update the DMARC record in your domain’s DNS.
Log in to your DNS management console.
Navigate to the domain where you’ll be publishing a DMARC record.
Most DNS management consoles will ask for:
Hostname: this should be _dmarc. NOTE: the leading “underbar” character is required!
Resource type: this is TXT, as DMARC records are published in the DNS as TXT resources.
Value: this is the DMARC record itself which includes your DMARC Policy.
Save and you’re done!
If you have multiple sending domains and want to get DMARC reports for all of them, repeat the process for each domain.
Once you’ve published a DMARC record, DMARC data will typically begin to generate within a day or two in the form of reports that give you insight into which sources are sending emails from your domain.
Step 4. Analyze DMARC Reports.
How do you read DMARC reports?
DMARC data gives you visibility into your internal email program and allows you to:
1. Inspect your sending sources.
DMARC reports will show you all the domains and IP addresses you’re using to send emails. As sender reputation is becoming increasingly relevant, it’s incredibly important to have full visibility into all your outbound email sources.
2. Monitor email authentication.
You can see if any of your mail senders are failing SPF, DKIM, and DMARC authentication.
3. Detect unauthorized use of your domains.
You can determine if there are any unauthorized third parties sending emails using your domains.
DMARC can send 2 types of reports upon request: aggregate reports and forensic reports.
The type of reports that will be sent to the domain owner is indicated in the DMARC record: rua= stands for aggregate reports and ruf= stands for forensic reports.
The GlockApps DMARC Inspector generates a DMARC record to receive both types of reports.
In the GlockApps DMARC Inspector, the reports are presented under the Aggregate Reports and Forensic Reports tab.
DMARC Aggregate Reports
Aggregate reports provide valuable visibility into the health of your email sending infrastructure and help you detect authentication issues and malicious activity.
These reports are sent in XML format and can be difficult for you to read and understand. The GlockApps DMARC Inspector processes aggregate reports and presents the information to the user in the format of a table where they can see all mail sources sent on behalf of the domain and percentages of the messages with SPF, DKIM, and DMARC pass/fail.
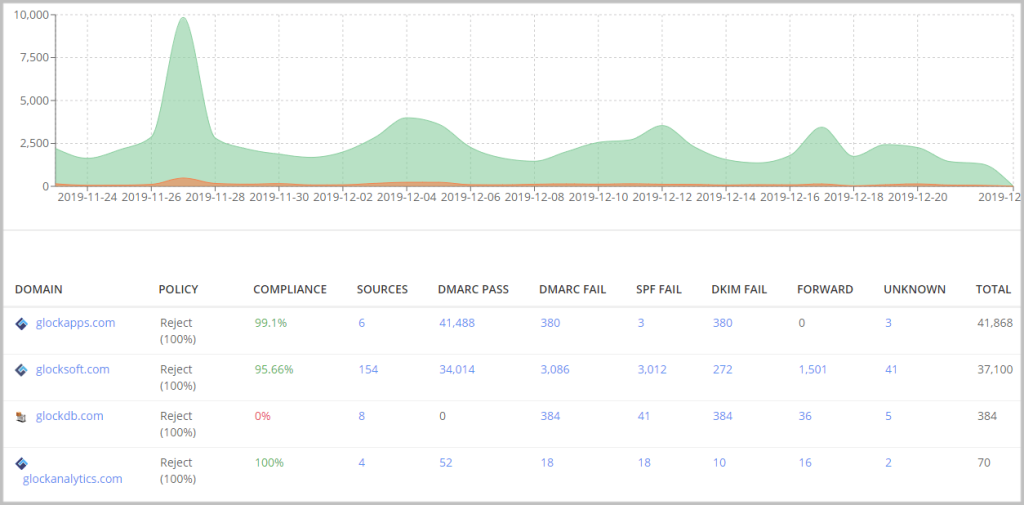
The picture below represents an example of the processed aggregate report in the GlockApps DMARC Inspector where
DOMAIN – the domains where you published a DMARC record to collect DMARC data.
POLICY – the policy applied to non-compliant messages used in your DMARC record for the domain.
COMPLIANCE – the percentage of DMARC compliant messages sent from the domain for the chosen period.
SOURCES – the number of sources (IP addresses) sending emails from the domain.
DMARC PASS – the number of DMARC compliant messages sent from the domain for the chosen period.
DMARC FAIL – the number of DMARC non-compliant messages sent from the domain for the chosen period.
SPF FAIL – the number of messages with failed SPF sent from the domain for the chosen period.
DKIM FAIL – the number of messages with failed DKIM sent from the domain for the chosen period.
FORWARD – the number of the email messages sent from the domain and then forwarded for the chosen period.
UNKNOWN – the number of source IP addresses that have sent emails for your domain, but have missed an SPF record or DKIM signature for your domain.
TOTAL – the total number of email messages sent from the domain for the chosen period.
Click on the domain name to see all the IP addresses sent on behalf of the domain.
The report shows the sending IP address and hostname, the DMARC, SPF, DKIM check (aligned/pass/fail), the applied DMARC policy, and the total number of emails sent by the host.
You can group the data by the sending IP, organization, host, or reporter.
If you see an unusually high number of sending sources, investigate the report to identify malicious senders.
Your authorized IP addresses are shown in green color. Unauthorized IPs are shown by the grey color. GlockApps performs a DNS-based check to determine authorized and unauthorized sending IP for the domain.
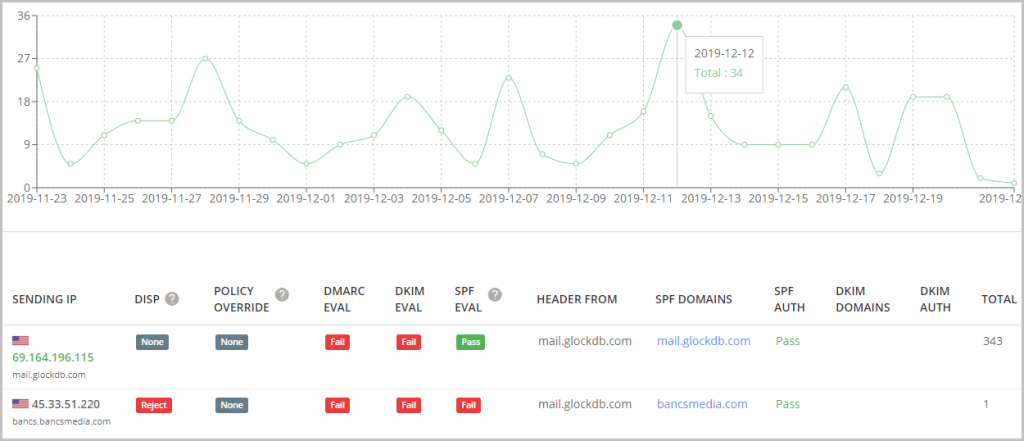
The main purpose of analyzing aggregate reports is to identify legitimate email sources which failed SPF or DKIM checks that is part of your sending infrastructure.
After you identify those legitimate senders which fail authentication checks, update your SPF/DKIM settings so that emails from them pass authentication next time.
And you’ll want to remove the hosts that are not supposed to send emails from your domain but are passing authentication if you see any.
Upload Reports
If you already have a DMARC report, you can upload it in GlockApps and our tool will parse it for you. You can upload a report in .zip, .gz, and .gzip formats.
Forensic Reports
DMARC forensic reports are generated by email service providers almost immediately after an email message fails DMARC authentication check.
A forensic report provides information about individual messages that didn’t pass authentication including the message Subject, source IP, reported domain, From and To email addresses, sending date, and failed authentication method.
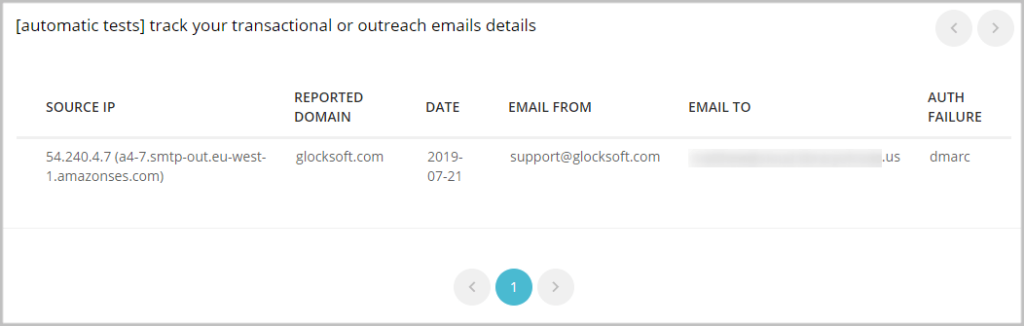
Move to Quarantine and Reject Mode
In the quarantine mode (p=quarantine), an email message that fails DMARC authentication is moved to the spam folder.
You can consider switching from the monitoring p=none policy to the p=quarantine policy in 3-4 weeks if you find everything fine and if all your legitimate senders pass email authentication checks.
Then if everything goes fine for 2-3 months, you can consider moving to the Reject mode.
In the reject mode, an email message that fails DMARC authentication is rejected and is never delivered. It’s the strictest action applied to emails that fail email authentication and provides full email protection against spoofing.
Learn More About DMARC Reporting:
What is DMARC: Email Security with DMARC, SPF, and DKIM
How to Protect Sender Domain with DMARC: Using DMARC Enforcement
How You Can Leverage the DMARC Inspector to Fix Deliverability Issues