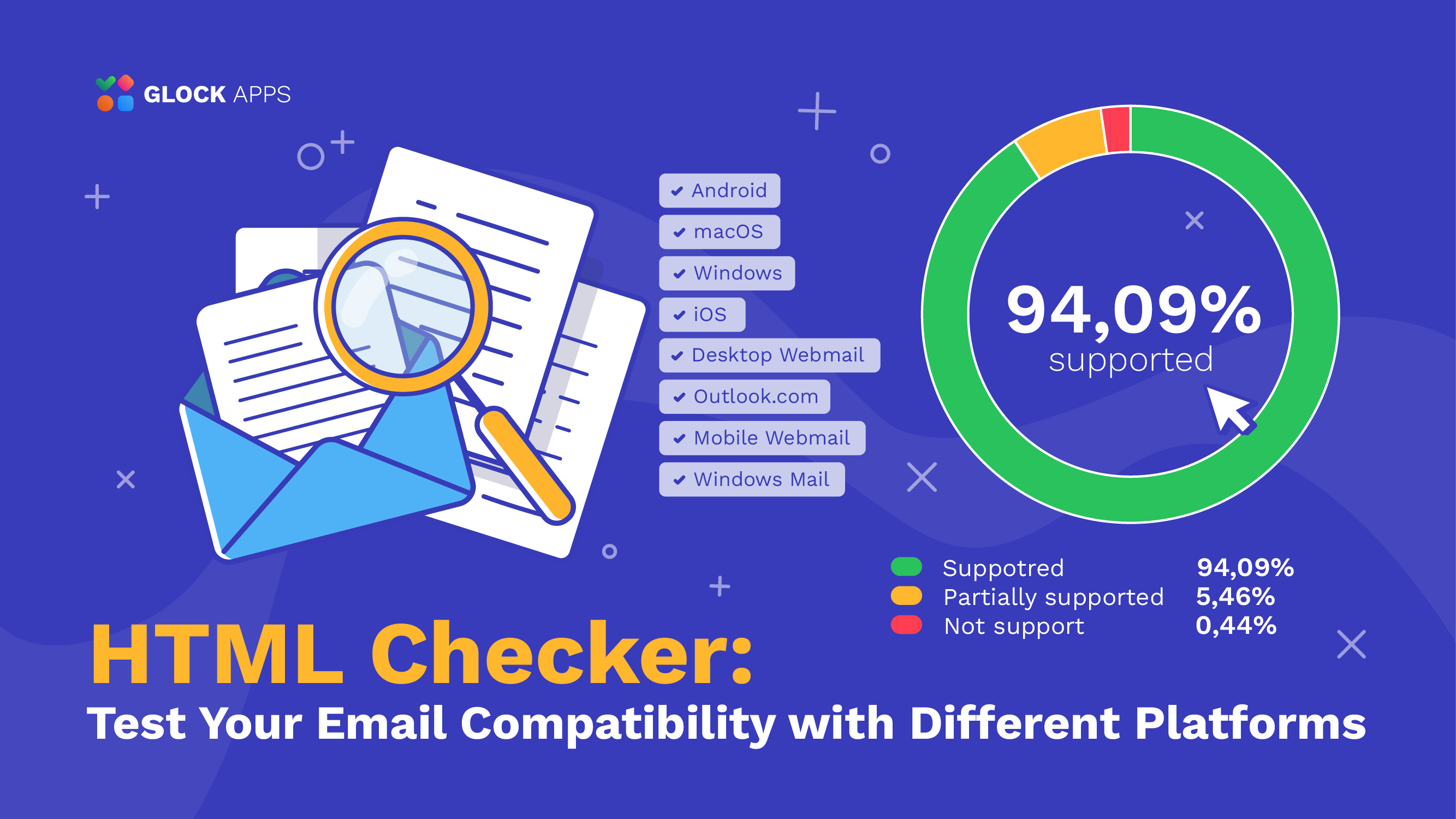
Email Spoofing Attacks in 2023

Email spoofing and phishing increased by 220% in 2021. With such high numbers, cyber-criminals are taking advantage of opportunities to spoof emails and phish for valuable information and credentials. As a result, the average cost of a data breach in 2021 was $4.24 million!
Types of Spoofing
There are many ways cybercriminals can attempt to steal your personal information. These are 8 types of spoofing:
Email Spoofing
- When a malicious sender forges email headers to commit email fraud by faking a sender’s email address. Email spoofing turns into a phishing attack when the hacker embeds the spoofed email with malicious links or an attachment that can install malware onto the recipient’s computer.
Caller ID Spoofing
- When a caller attempts to disguise their identity by falsifying the phone number sent to your caller ID screen during phone calls. They use these spam calls to try and trick you into giving away confidential information.
Domain Spoofing
- When a hacker appears to utilize a company’s domain to impersonate the company or one of its workers.
IP Spoofing
- When a hacker modifies the packet header’s source address to make the receiving computer system think the message is from a trusted source and not from a spoofed IP address.
DNS Spoofing
- When a scammer uses altered DNS records to redirect online traffic to a spoofed website that looks identical to the real one.
GPS Spoofing
- When someone is broadcasting fake signals to a receiver antenna via a radio transmitter to counteract a genuine GPS satellite signal.
Address Resolution Protocol (ARP) Spoofing
- When an attacker attempts to bypass network access controls in order to change the relationship between Media Access Control (MAC) addresses and Internet Protocol (IP) addresses. The outcome is that they appear to be someone else to all of the other devices on your network, allowing them access to all of the traffic intended for the genuine user.
Website Spoofing
- When cybercriminals develop a website that resembles a well-known brand, as well as a domain that is almost identical to a corporate’s web address, they are able to fool the majority of internet users into visiting their spoofed websites.
It is hard to overestimate the need for cyber-security in 2023. As we switch to a digitalized society, the question of security for every business became even more important and, at the same time, more difficult to achieve. As the security of an email is often overlooked, it can lead to dreadful consequences.
It’s a serious mistake, and an enormous benefit for the attackers, to believe that only huge businesses are targeted by email spoofing and phishing. 42% of organizations, involved in cyber-breach were small and medium businesses.
Cyber-breaches can come in all shapes and sizes, so why exactly email? Because 94% of all malware gets to a computer via email.
To better understand email spoofing, let’s look at how a cybercriminal could try to (unsuccessfully) spoof GlockApps.
What is Email Spoofing?
Email spoofing attacks occur when a cybercriminal attempts to commit email fraud by forging someone else’s identity via email. Then, they use that forged sender address to try to convince a recipient to perform some action so that they can gain access to that recipient’s personal and private information. Usually, spoofers pretend to be a person or an organization that the recipient would trust.
To perform an email spoofing attack, the malicious sender has to compromise the SMTP(Simple Mail Transfer Protocol), which isn’t hard because it was created without any security precautions. Usually, spoofers take advantage of the email header components: “From” field, “Return-path”, and “Reply-to”.
Example of Email Spoofing
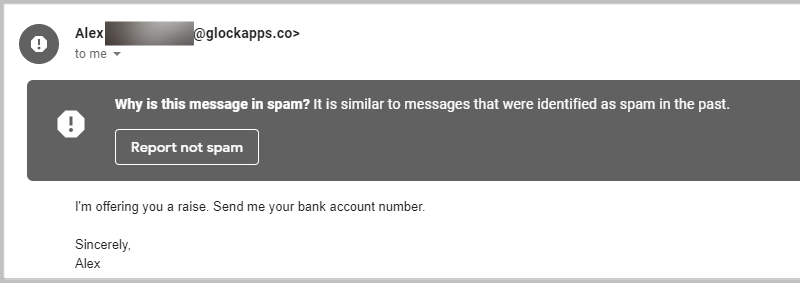
We tried to replicate how a spammer could have sent a fake email message offering a monetary raise to GlockApps in exchange for sensitive information. In Gmail, for example, this spoofed email would most likely not appear in the Inbox and would be marked as probable spam.
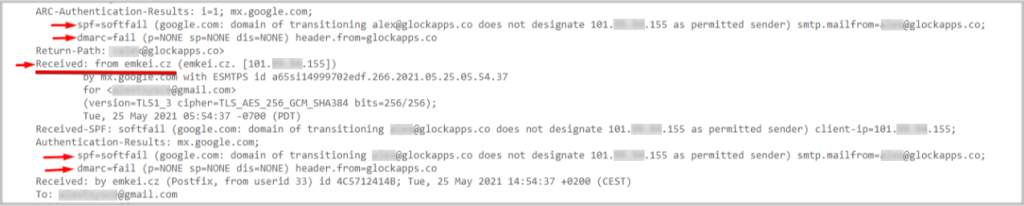
If you suspect a suspicious email, go to the three vertical dots section (More) on the right of the email header -> click Show original, to see details from spoofed messages that are invisible at first sight. There you will see all the details related to the message including: the message ID, “From” address, as well as the results of SPF and DMARC checks.
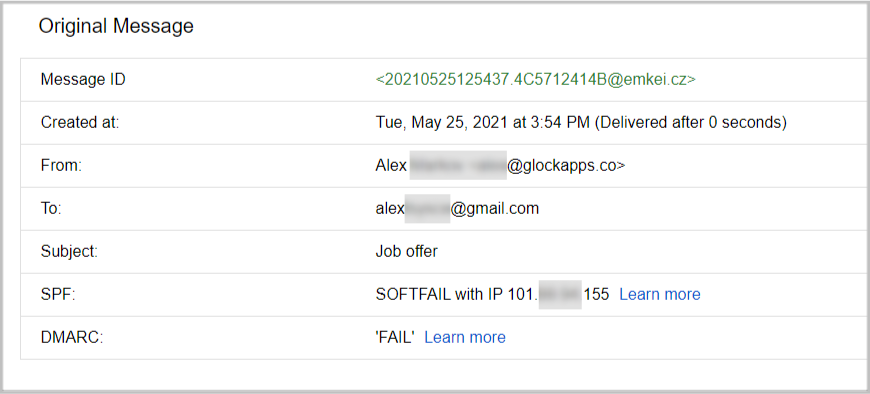
As you can see from the Original Message report, SPF shows “softfail” and DMARC authentication – “fail”. Also, notice how the message ID shows that the message that was sent from “Alex” was actually sent from emkei.cz. This is a clear indication that the email is not genuine.
Human error plays a massive role in spoofed emails since not many recipients check beyond the email headers for the legitimacy of the email. Especially, if the email looks trustworthy, sounds urgent, or comes from a seemingly legitimate source (someone they know).
So what happened when a malicious agent tried to spoof our domain?
First, we received DMARC analyzer warning alerts.
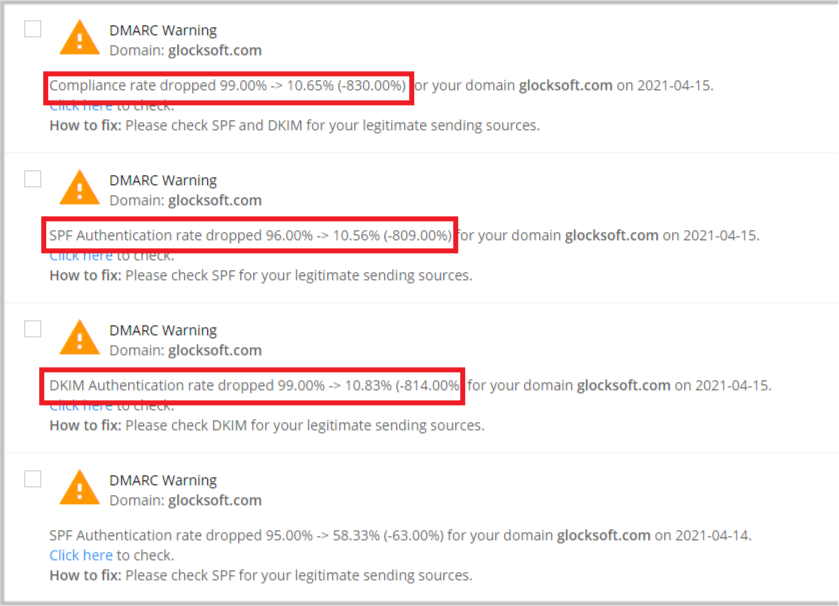
As you can see, the SPF, DKIM authentication, and compliance rate have all decreased significantly in one day (from around 90% to 10%). Therefore, we went to our DMARC reporting dashboard and this is what we saw.
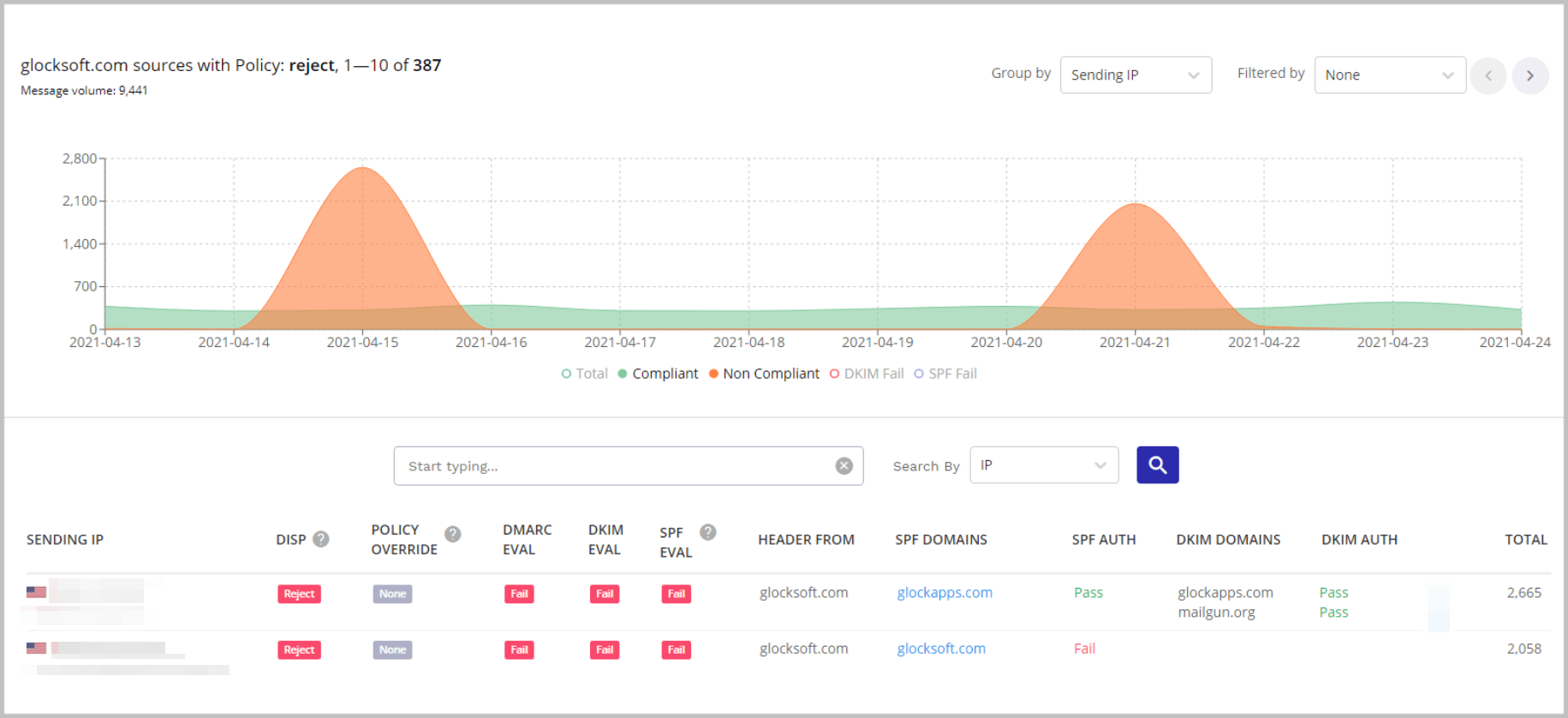
Our DMARC reporting dashboard looked like two islands in green water. Green is our usual domain traffic, whereas the islands – you guessed it – are the spoofing attacks.
How to Protect Yourself from Spoofing Attacks
Today there are three commonly used email security protocols to help protect you from scammers sending spoofed email messages: SPF, DKIM, and DMARC.
SPF
Sender Policy Framework is the oldest email security protocol. It is a simple TXT record in your DNS (Domain Name System) that contains all the IP addresses and sender addresses that are allowed to send emails on your behalf. Therefore, only the email sender address and the IP addresses stored in your DNS will allow SPF authentication to pass.
So, ideally, if a message fails SPF authentication, it could mean that someone was trying to use a fraudulent sender address to abuse your domain and send unsolicited messages pretending to be you. Although SPF has its downsides and failure could also mean that your record is misconfigured, it still is a red flag.
DKIM
DomainKeys Identified Mail is an email authentication standard that uses public-key encryption to authenticate email messages. Simply put, it signs your emails to make sure it wasn’t altered in the process of sending from sender to recipient\.
DMARC
Domain-Based Message Authentication, Reporting, and Conformance is the protocol that is used for maximum protection as it works on top of the previous protocols to enhance your email security level. DMARC provides you with reporting, making it easy to see what is happening with email traffic on your domain. You gain full visibility over who is sending emails on your behalf, as well as choose a policy that will apply to suspicious emails.
You can choose from the following DMARC policies:
- None – nothing will happen
- Quarantine – suspicious emails go to spam
- Reject – unsolicited mail is getting blocked
So, to sum it up, SPF dictates who is allowed to send on your behalf, DKIM makes sure email is not altered in the process, and DMARC aligns these two, allowing you to choose what to do with suspicious emails, and provides you with reports and visibility.
With all these 3 measures of security helping you combat email spoofing, scammers are will have a harder time trying to spread malware and conduct data breaches.
Read more: Email Authentication: the Ultimate Guide
In this particular attack, the SPF evaluation failed because the attacker was using a fake email address that didn’t match the “Header From” domain. The IP address was also not included in the SPF record. So you see, these security protocols work perfectly together.
Now, if you have implemented DMARC with the reject policy, the good news is that you will not need to do anything about the attack since it isn’t going through your mail server and your clients are not receiving these spoofed emails.
Do Not use DMARC “None” Policy to Prevent Business Email Compromise
Many people make the mistake of assuming that they can block spam and phishing emails by implementing DMARC with a “none” policy. In reality, this policy is only needed during the first stages of implementation to gain visibility and make sure you’re not blocking any legitimate sources. But what happens to a spoofing attack if you have a none policy?
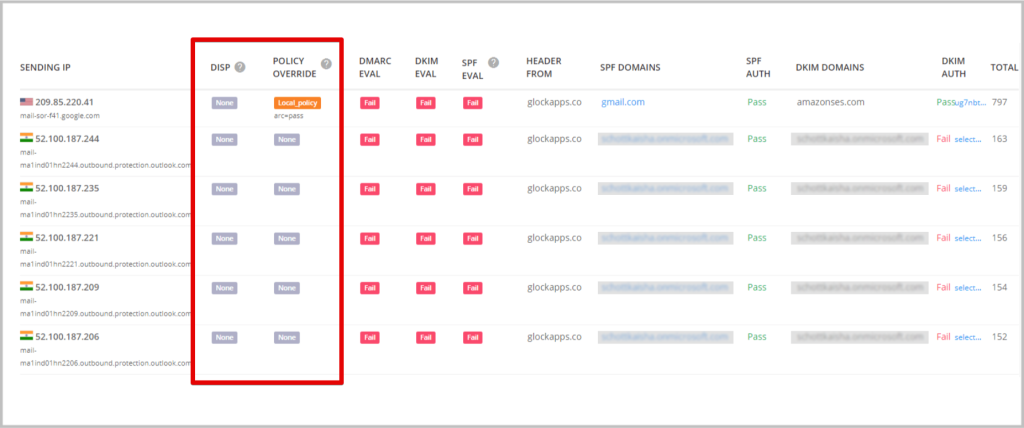
In the screenshot, although DKIM has failed authentication, the unsolicited outgoing messages were not quarantined or blocked from being sent to the receiving user inboxes because the DMARC policy was set to “none”.
How to Know if You’re Being Spoofed
DMARC Report Analyzer
First, we recommend using tools that receive DMARC reports and gain full visibility into your domain traffic or at least make a private email address dedicated to receiving reports. But remember, that they come in an XML format, created to be read by machines, not humans. That is why tools, like GlockApps DMARC Analyzer, are so much better. Apart from storing thousands of reports, they translate them in a comprehensive human-friendly format and send you notifications if something goes wrong.
Start using our DMARC Analyzer right now with 10,000 free monthly DMARC messages and unlimited domains. We’ll help you with our support team, guides, and in-depth analytics.
Bounced Emails
DMARC reports start coming in within 24 hours of sending an email message. But is there a way to know that you are being spoofed immediately? Yes, all you need to do is track your bounced messages. When a message is not delivered, usually it bounces back and you receive an email with an error and, sometimes, the reason. For example:
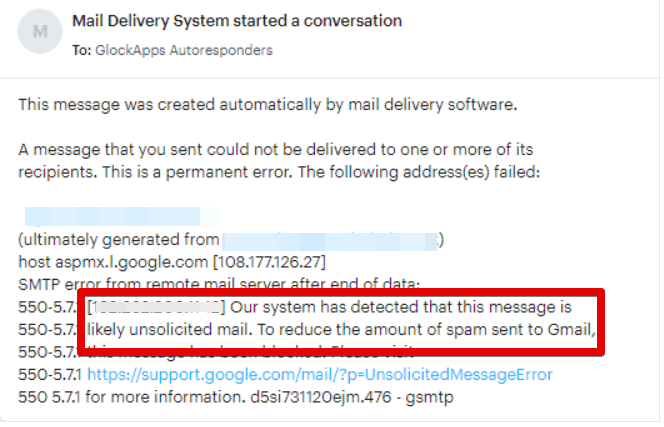
If you follow email list best practices, don’t buy any email lists that can contain spam traps. A spike in bounced emails should be a warning sign that you may be getting spoofed at that moment. Red flags could also be identified by your recipients (if they start receiving weird or suspicious emails from you).
Google Postmaster Tools
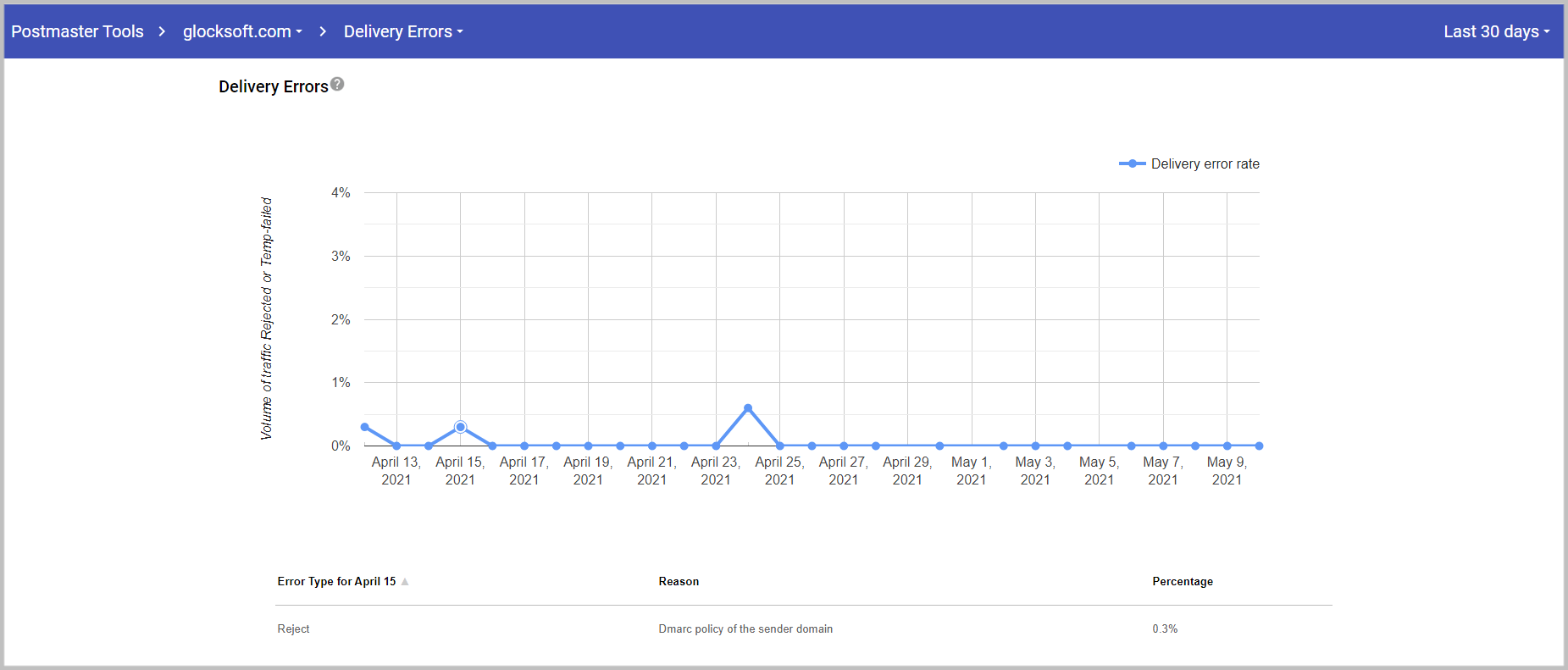
Google gives you a great opportunity to see spam reports, delivery errors, feedback loops, sender reputation, and more. If you are a legitimate sender and you follow email best practices, your sender reputation should be high. When an email gets spoofed – the sender’s reputation goes down very fast. You can end up with a low spammer reputation and zero recipient trust within days.
Google Postmaster also shows your delivery errors, where you can see spikes in bounced emails.
Email Spoofing Takeaways
Cybercrime in 2023 should not be taken lightly. As everything that involves spoofing emails skyrockets, be sure to protect yourself and your assets from identity theft. Email should be protected just as any other network since a vast amount of malware gets onto computers through email.
Email spoofing is one of the most common cyber-attacks. However, if you’ve become victim to any types of spoofing including: Caller ID spoofing, IP spoofing, website spoofing, etc, notify the FCC, the FTC, or even your local police department to report the crime.
The best way to prevent email spoofing is to protect yourself by implementing 3-layered protection: SPF, DKIM, and DMARC. And although this is not a silver bullet from cyber-attacks – it is the best chance to protect your email from email spoofing these days.
More tips to help you prevent spoofing:
- Be sure to use a secure email provider to send messages from.
- Be careful when using a password manager that stores your autofill login credentials and passwords.
- Never give aways sensitive data over the phone or through email.