DMARC Fail: What Causes DMARC Failure in 2025?

There are several causes for DMARC failure. To ensure your emails are properly authenticated and your domain is protected from cybercrime such as spoofing, it’s critical to understand what caused DMARC to fail authentication.
Last year’s cyber-attacks showed how unprepared businesses worldwide were. Although Google tries its best to block over 100 million spam messages every day, companies have lost millions of dollars in financial losses due to cybercrime.
Spam comes in all shapes and sizes, so why are we so concerned about DMARC email authentication?
94% of all malware is downloaded to a computer via email, and the majority of people are not able to distinguish between a well-crafted phishing email and legitimate messages. DMARC, along with SPF and DKIM, helps you monitor who is sending messages from your email domain and protects your customers from phishing, spoofing, and other email scams.
This article will show you how you can avoid DMARC failure and improve cybersecurity for your business.
We will cover:
- How Does DMARC Work?
- DMARC Policy Options Used Around the World
- What Causes DMARC Fails?
- How to Find out if Your Message Failed DMARC
- Tools to Help You Recognize DMARC Failing
How Does DMARC Work?
Domain-based Message Authentication, Reporting & Conformance (DMARC) is used for 3 reasons:
- DMARC allows you to see what email senders are pretending to be you and helps prevent spoofing attacks.
- Your DMARC record instructs receiving servers (AOL, Outlook, Yahoo! Mail, Gmail, and other Internet Service Providers) on how to handle messages that do not pass DMARC checks: whether to send them to the spam folder or block the mail altogether.
- DMARC improves your email deliverability by showing email receivers that you’re a reputable sender with authenticated emails.
Here is a diagram to show you how DMARC works:
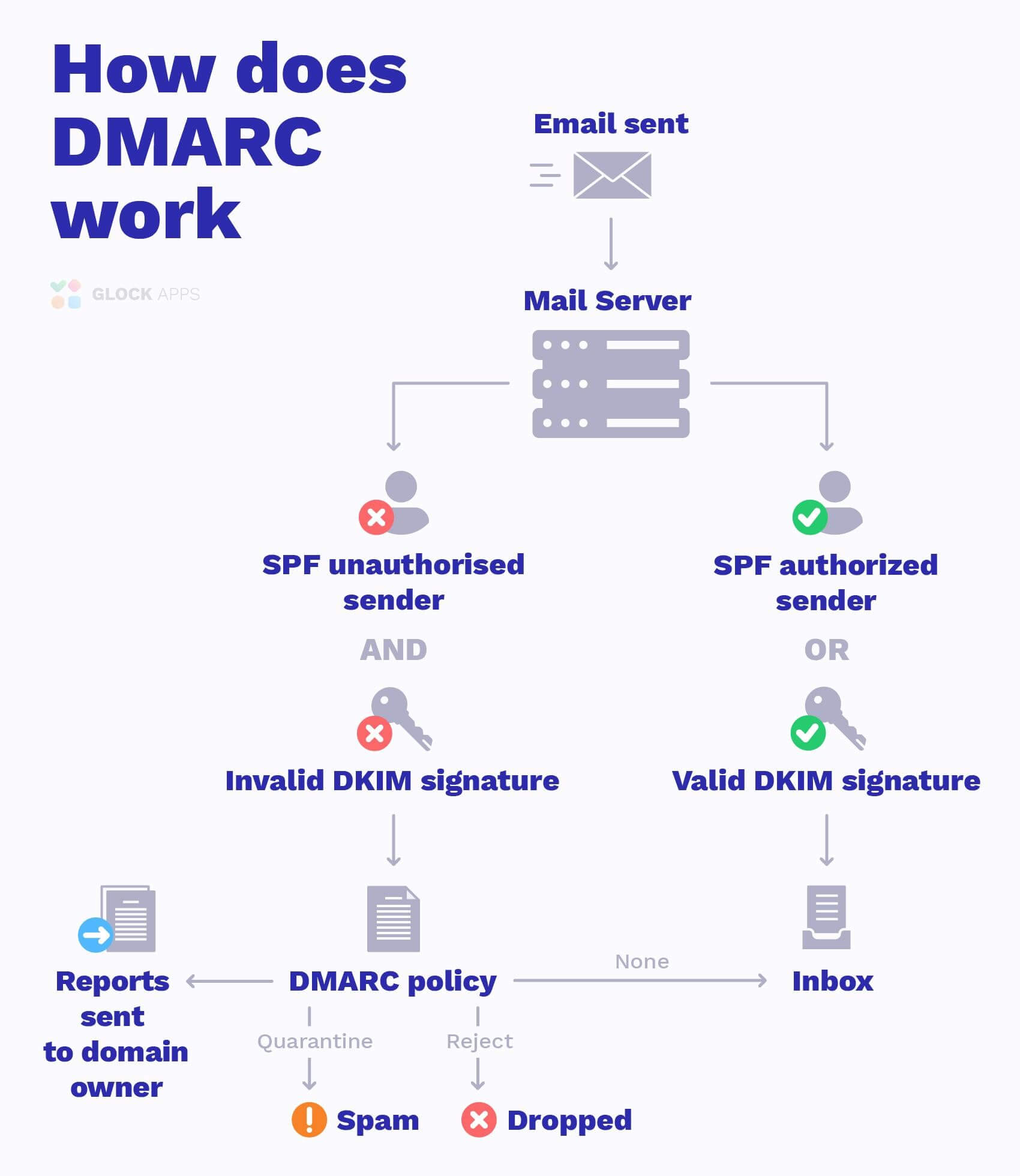
DMARC Policy Options
DMARC is a third layer of protection (after SPF and DKIM), that was introduced 9 years ago. Even so, a significant number of businesses worldwide fail to implement DMARC properly, and most of those who do, only adopt a p=none policy.
Is your DMARC Record Configured Correctly?
This chart shows active DMARC record policies being used across the world according to the data collected by DMARC.org:

DMARC Policies Usage
As you can see from the chart above, the majority of businesses that move forward with DMARC adoption only get as far as the p=none policy. Unfortunately, that DMARC policy is only needed in the early stages of implementation and does not defend against cyber-attacks.
Learn More about DMARC Policies: What is DMARC: Email Security with DMARC, SPF, and DKIM
So what stops businesses from fully applying DMARC authentication?
What Causes DMARC Fails?

In theory, in order to avoid failing DMARC and ensure that your email passes DMARC compliance, all you have to do is: implement SPF, DKIM, and DMARC. You also have to make sure SPF and DKIM align during authentication check and voila! Sounds simple enough, right?
But in reality, there are quite a few roadblocks on the way that can cause your message to fail DMARC:
Message Failed DMARC Authentication Because of SPF Authentication
In order to become DMARC compliant, it’s important that you define which IP addresses will send emails on behalf of the domain owner in your SPF record prior to sending your first email campaign. You can do this by including a TXT record name in your domain’s DNS record.
If you are unsure about how to do this, contact your DNS provider or read: How to Create SPF Record & Optimize it
DMARC will perform an SPF check to verify if the sending source is authorized to send messages.
SPF 10-DNS-Lookup Limit
If your SPF record exceeds the 10-DNS-lookup limit, SPF email authentication issues a permanent error stating “too many DNS lookups.” DMARC considers this a fail.
Therefore, when your SPF record reaches this limit, and DKIM also fails, your emails will fail DMARC authentication, which means your emails are not properly authenticated and might not reach the inbox.
No DKIM Authentication Can Fail DMARC
It is equally as important to set up DKIM authentication before you send out your first email campaign.
Another reason why your message might fail DMARC is because you haven’t created a DKIM signature for your domain. In such situations, your email service provider creates a default DKIM signature for outgoing emails that doesn’t match the domain name in your From header address.
Your recipients’ mail servers will perform DMARC and DKIM checks and will fail to verify that the two domains match. Hence, DKIM and DMARC will fail for your message.
DMARC Failing Because of Forwarded Emails
SPF is the oldest protocol, introduced back in 2000 and it has quite a few downsides. One of them is the inability to pass authentication checks after email messages are forwarded.
If your message fails DMARC, it may be because it was forwarded after you sent out your email campaign.
SPF and DKIM Should Align to Avoid Failing DMARC
Once you have SPF and DKIM (DomainKeys Identified Mail) implemented for your domain, DMARC authentication checks for domain alignment in order to pass DMARC.
What does this mean? Either SPF (written in your SPF record within your domain’s DNS) or DKIM (the domain name signed with your DKIM signature) have to be the same as the domain in the From header address. However, many would argue that the best practice is to try to align with both SPF address and DKIM signature, otherwise, you may see spikes in bounce rates.
Read also:
DMARC Monitoring and Reporting: Step-by-Step Guide
The Ultimate Guide to Email Authentication
How Do You Know if Your Message Failed DMARC?
We mentioned just a few of the purely technical roadblocks that can cause your message to fail DMARC.
SPF, DKIM, and DMARC were created in a form of simple TXT records in your domain’s DNS, which is very practical. Any error can result in failures regardless of you implementing the ‘quarantine’ or ‘reject’ policy.
We reiterate that it’s critical to be informed when your messages are failing DMARC.
With a failing DMARC or the wrong policy, you run the risk of your email marketing campaigns and other legitimate messages being blocked or ending up in a spam folder. For big corporations, disruption of important email communication can result in significant financial losses as well as a tarnished sending reputation.
Lacking these important email authentication methods also makes you a target for spoofers attempting to send spam with your domain name.
Aside from checking your messages’ email header to see if it passes DMARC checks, you can use DMARC report analyzing tools to be immediately informed of any problems with your DMARC record, email authentication, and email traffic.
Tools to Help You Recognize DMARC Failing
Even as your company works through the first stage of DMARC email authentication with a ‘none’ policy, your will start to receive a lot of incoming data on your domain traffic.
DMARC forensic reports were not created to be easily readable by humans; they come in XML format. Furthermore, a company receives one report for each server it sends an email message to. The more emails you send, the more DMARC reports you’ll receive. So the number of reports could reach thousands each day.
In such cases, it is highly recommended to use a DMARC Report Analyzer to collect, analyze, and store those reports.
Start using the GlockApps DMARC Analyzer today with 10,000 free monthly DMARC messages and unlimited domains. We’ll help you on your DMARC journey with our support team, guides, and in-depth analytics.
Conclusion
With all this in mind, can we excuse companies for leaving their domains unprotected? Of course not.
Setting up your DMARC record is equally as important as defining an authorized legitimate domain in your SPF TXT record and setting up your DKIM key. Applying all three protocols is the best way to authenticate your emails.
Failing to safeguard your domain’s reputation can result in days or weeks of brand damage, compromised business emails, stolen credentials, and potentially significant monetary losses.
Although DMARC is not a flawless solution, it is the highest protection one can acquire for their business domains. In the end, everyone will benefit from sending emails that are identified as legitimate.



