Authenticate Emails with DMARC for Better Deliverability

Email is a wonderful opportunity for businesses to promote their brand and get clients. On the other hand, email facilitates the spreading of spam, phishing, malware, viruses and other fraud simply because it is difficult to tell if the sender is really the one it pretends to be.
Legitimate senders have to wade through complicated anti-spam filters just to get their emails delivered to the destination user.
To help email senders deliver legitimate emails to the recipients and block phishing and fraud messages, a new email authentication standard was adopted by email senders and receivers.
1. What is DMARC?
DMARC stands for Domain-based Message Authentication, Reporting & Conformance. It is a mechanism to determine whether an email message is coming from a particular sender or not. It is designed to protect the company’s email domain from being used for email spoofing, sending phishing scams and other malware.
DMARC is built on the widely deployed SPF and DKIM protocols and adds domain alignment checking and reporting capabilities. DMARC reports are generated by the organizations that process incoming emails and give domain owners visibility on how their domains are used on the Internet.
Senders and organizations use DMARC to check that their sending domains are not abused and that they don’t send any fraud emails.
By implementing the DMARC authentication, email senders can make sure that they did everything they could to prevent the abuse of their domains, stop spoofed messages and protect their brand.
2. Why is DMARC Important?
To tie all of the above, DMARC provides the following benefits to domain owners:
2.1. Prevention of fraud emails.
If you implement DMARC and make all of your legitimate email sources DMARC aligned, you can tell the email receivers to reject any email that claims to come from your domain but fails DMARC. DMARC gives you powerful anti-phishing control and has been used to block huge amounts of email fraud.
2.2. Simplified delivery to the recipient’s Inbox.
DMARC makes it easy for email receivers to identify the message. To stop spam, email receivers invest a lot of time, money, and resources in developing technology that filters out unwanted emails. The DMARC adoption allows email receivers to simplify their filtering rules, quickly identify the email and deliver it. If an email passes DMARC authentication, it means it truly comes from the domain displayed in the From address.
2.3. Protection of the domain and brand reputation.
By analyzing DMARC reports, you can identify illegal senders using your domain and tell the receivers to reject an email sent from your domain if it doesn’t pass the DMARC check. This way you can reduce the number of unsolicited emails coming from your domain that can hurt your sender reputation, brand, and ROI.
2.4. Email traffic control.
The deployment of DMARC allows you to have full control over your email sources and make sure that they send only legitimate messages that your subscribers want. You can see whether or not your legitimate sending sources pass the SPF and DKIM check and you can fix the authentication issues when they occur. Organizations can use DMARC to monitor how their partners send emails on their behalf and if everything is sent correctly. This allows you to reduce the risk of having your sending IP/domain blacklisted for sending spam emails.
2.5. Easier email visibility and brand recognition.
DMARC enforcement allows you to use the BIMI standard for displaying your logo next to your messages in the recipient’s inbox. BIMI helps the recipient recognize your emails in the croud and be sure that the email truly came from you and not from someone pretending to be you. Currently, the BIMI standard is supported by the Yahoo mailbox provider only, but it is going to be supported by other ISP in the coming year, too.
DMARC becomes a “must-have” for anyone who cares about email deliverability. If your emails are not DMARC compliant, they are competing with spam and fraud emails for a place in the user’s Inbox.
3. How does DMARC Work?
DMARC is built on the base of the two other authentication methods SPF and DKIM.
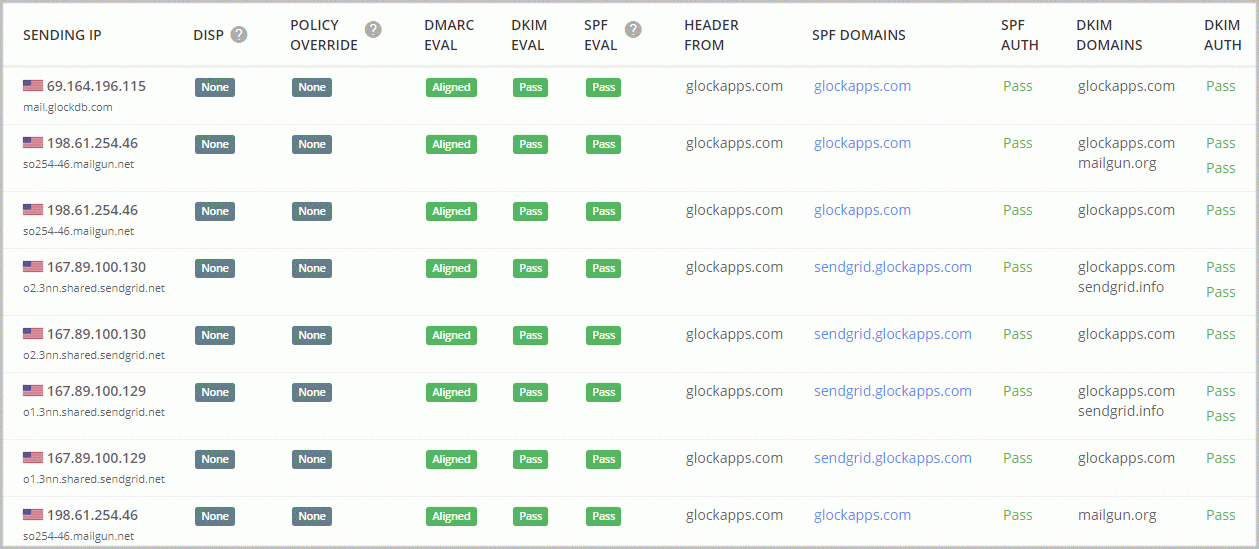
SPF and DKIM authenticate various aspects of an email message: SPF authenticates the domain that appears in the “Envelope From” address, and DKIM authenticates the domain found in the d= tag inside a DKIM-signature in the email header.
These domains are typically not visible to the recipient which makes it possible to spoof the email “From” address.
The results of SPF and DKIM checks create the Authenticated Identifiers.
In the case of SPF, identifier alignment means that the domain of the “Envelope From” address has to align with the domain in the header “From” address. When the “Envelope From” address is empty, alignment is checked against the EHLO domain.
In the case of DKIM, identifier alignment means that the domain found in the d= field of a DKIM signature in the email header has to align with the domain found in the header “From” address.
There are two modes in identifier alignment: strict and relaxed.
The strict mode requires the two domains to be identical in order for them to be in alignment. For example, domain.com aligns with domain.com in strict mode, but it doesn’t align with mail.domain.com.
The relaxed mode doesn’t require the two domains to match exactly. As long as the organizational domains match, they align with each other. For example, domain.com aligns with domain.com and also aligns with mail.domain.com.
Because anyone can register a domain and set up SPF and DKIM, DMARC hardens the authentication process by connecting the results of processing SPF and DKIM — the Authenticated Identifiers — with the header “From” field. The Authenticated Identifiers have to be related to the domain found in the “From” header field. This concept is referred to as “Identifier Alignment”.
When the following conditions are true for an email message, the email is DMARC aligned:
- SPF authentication passes and has identifier alignment; and/or
- DKIM authentication passes and has identifier alignment.
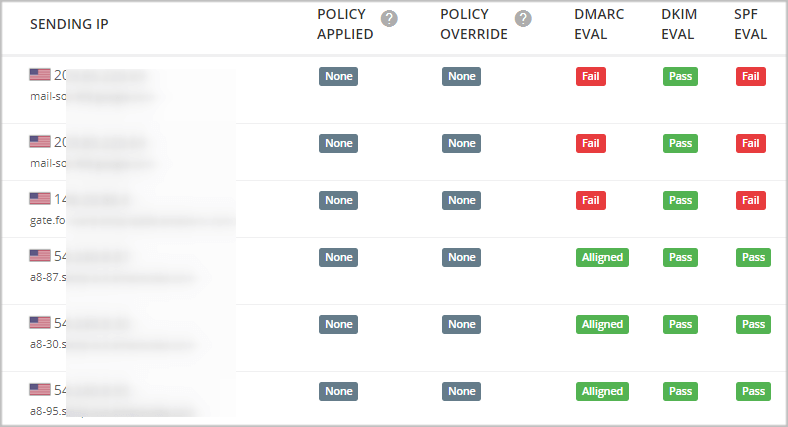
When an email is DMARC aligned, it passes DMARC authentication. It means that the email is truly sent from the email address displayed to end users.
3.1. What is DMARC Policy?
DMARC allows you to tell the email receiver how to handle an email if it fails the DMARC authentication.
There are 3 policies:
- none, also called the monitoring mode, (no action is taken, recommended to collect DMARC reports);
- quarantine (the email is moved to the spam folder);
- reject (the email is rejected outright and is never delivered).
You specify the DMARC policy in a DMARC record, where the policy appears in the p tag, like p=none.
3.2. What is DMARC Record?
DMARC record is a version of the Domain Name System (DNS) TXT record added to the domain to help the receiver manage emails based on a sender’s domain reputation. DMARC record is the implementation of DMARC policy on your domain.
3.3. What is DMARC Report?
DMARC provides reporting capabilities to allow email domain owners to gain visibility into how their email domain is used across the Internet and which email sources are sending from it.
The feedback comes in the form of a report, which is sent by the incoming email processor to the email address specified in the DMARC record, for example, rua=mailto:support@domain.com.
You can receive 2 types of reports: aggregate reports (stand for the rua= tag in the DMARC record) and forensic reports (stand for the ruf= tag in the DMARC record).
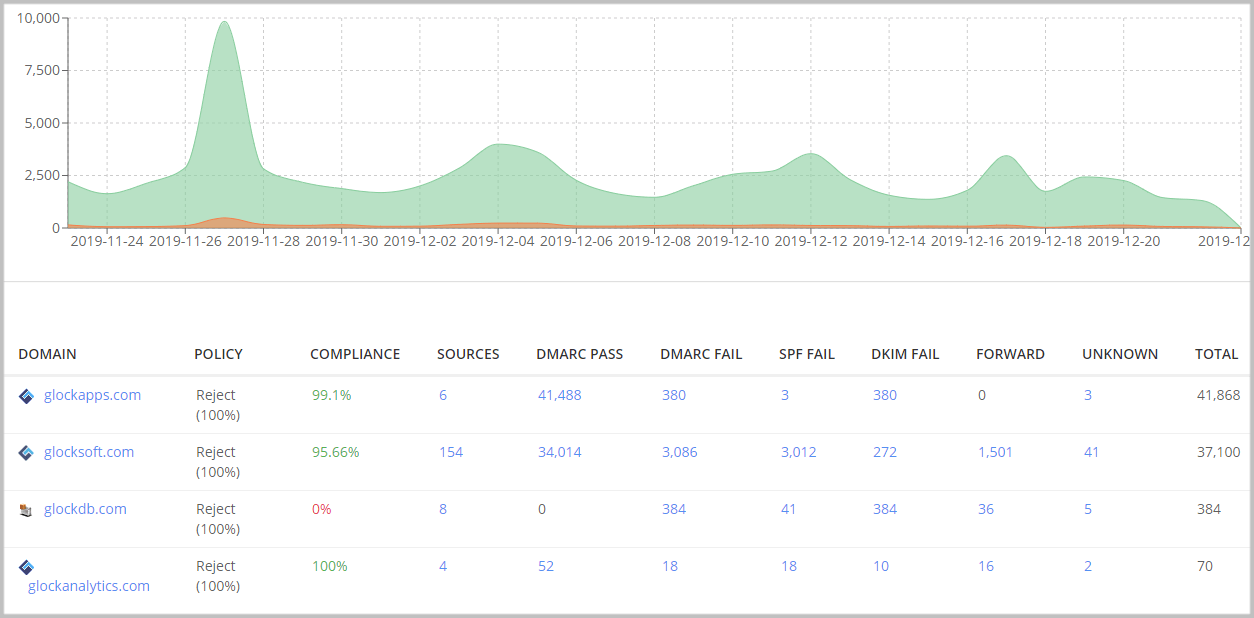
DMARC aggregate reports provide a comprehensive view of all of a domain’s traffic: sending sources, percentages of emails passing/failing SPF and DKIM, percentages of emails DMARC compliant and non-compliant.
Aggregate reports provide valuable feedback about the health of your email domain, help you determine authentication issues, identify illegal sending sources and stop malicious activity.
4. How to Set up DMARC
The process of setting up DMARC for your outgoing emails is simple:
- Create a DMARC record.
- Publish the DMARC record to the DNS of your domain.
- Analyze the data and modify your sending sources as appropriate.
You can use the GlockApps DMARC Analyzer tool to verify if your domain is protected with DMARC or not.
4.1. How to Create a DMARC Record
To set up a DMARC record, follow these steps:
Set up SPF and DKIM records
DMARC is built on the base of SPF and DKIM protocols, and it is impossible to implement it without the other two.
Verify your domain alignment
Make sure that your domain name is identical in ‘From: header’, ‘d=domain’ in DKIM signature, and ‘Return-path’.
Know your way about DMARC tags
A DMARC record consists of DMARC tags. The below list shows what each tag possibly found in a DMARC record means:
v: DMARC protocol version. The default is “DMARC1”.
p: policy applied to an email sent from the domain that fails the DMARC check. Example: p=quarantine.
sp: policy applied to an email sent from the subdomain that fails the DMARC check. Example: sp=reject.
pct: percentage of messages subjected to filtering. Example: pct=20 tells email receivers to only apply the ‘p=’ policy 20% of the time against emails that fail the DMARC check. This only works for the “quarantine” and “reject” policies.
rua: reporting URI of aggregate reports. Example: rua=mailto:agg_reporting@domain.com.
ruf: reporting URI of forensic reports. Example: ruf=mailto:for_reporting@domain.com.
fo: forensic options. Allowed values: ‘0’ to send reports if both DKIM and SPF fail, ‘1’ to send reports if either DKIM or SPF fails, ‘d’ to send a report if DKIM failed and ‘s’ if SPF failed.
rf: reporting format for forensic reports.
adkim: Alignment Mode for DKIM. Allowed values: ‘r’ (Relaxed) or ‘s’ (Strict).
aspf: Alignment Mode for SPF. Allowed values: ‘r’ (Relaxed) or ‘s’ (Strict).
ri: reporting interval for aggregate XML reports in seconds. Example: ri=86400 – 24 hours, ri=3600 – 1 hour. Normally ISP send DMARC reports daily, but they can send them on different intervals.
Examples of DMARC records:
v=DMARC1;p=none; rua=mailto:dmarc-report@domain.com
v=DMARC1;p=reject;pct=100;rua=mailto:agg-report@domain.com
v=DMARC1;p=reject;sp=reject;pct=50;adkim=r;aspf=r;fo=0;ri=3600;
rua=mailto:dmarc-report@domain.com
v=DMARC1;p=quarantine;pct=100;adkim=r;aspf=r;rua=mailto:agg-report@domain.com;
ruf=mailto:for-report@domain.com
Publish the DMARC record at the DNS of your domain
A final step in creating your DMARC record is implementing it into DNS.
4.2. How to Add a DMARC Record
To add a DMARC record you have to contact your DNS administrator. He will create a TXT record with your DMARC record and add it to DNS.
After adding your DMARC you will be all set and ready to receive reports from the domains you have chosen.
When implementing DMARC for the first time, we strongly recommend that you ramp up your level of protection using DMARC slowly by employing the DMARC policies in this order.
Start with the “none” policy to collect information about your sending streams and authentication data. Analyze the reports and look for anomalies such as an abnormally high number of sending sources and not signed messages which are probably being spoofed.
When you identify and delete all illegal mail streams and make sure that legitimate senders pass SPF, DKIM and DMARC checks, change the policy to “quarantine”.
Again, monitor the results. When you are absolutely certain that all of your messages are signed, change the policy to “reject” to add the highest level of protection. Check the reports regularly to ensure everything is going well.
Similarly, you can use the optional “pct” tag to increase and test your DMARC deployment. This setting works with the “quarantine” and “reject” policies. Start with a low percentage and increase it every few days.
So, the full DMARC deployment process could be like this:
Day 1 – p=none pct=100 (monitor all)
Day 20 – p=quarantine pct=1 (quarantine 1%)
Day 23 – p=quarantine pct=5 (quarantine 5%)
Day 26 – p=quarantine pct=10 (quarantine 10%)
Day 30 – p=quarantine pct=25 (quarantine 25%)
Day 35 – p=quarantine pct=50 (quarantine 50%)
Day 50 – p=quarantine pct=100 (quarantine all)
Day 60 – p=reject pct=1 (reject 1%)
Day 65 – p=reject pct=5 (reject 5%)
Day 70 – p=reject pct=10 (reject 10%)
Day 75 – p=reject pct=25 (reject 25%)
Day 80 – p=reject pct=50 (reject 50%)
Day 100 – p=reject pct=100 (reject all)
Always, review your daily reports to notice any abnormal behavior and fix the issue.
5. Do I Need DMARC?
According to Barracuda’s research, fake sender identity is a basis for almost 90% of email attacks. These attacks can be prevented with email authentication and DMARC is the essential protocol for sender identity authentication.
As stated at the official DMARC website, many Fortune 500 companies – American Express, Bank of America, Facebook, FedEx, Microsoft, Netflix, PayPal, and others, have strong DMARC policies, and the number of valid DMARC policies increased by 300% over 2019. Consumers want to be sure that if they provide information to a certain organization, they will not fall as victims to email fraud.
DMARC benefits for your brand:
- Fraud emails prevention;
- Easier delivery to the client’s inbox;
- Domain and brand protection;
- Control over email traffic.
DMARC not only prevents domain spoofing but also makes sure that your emails will be delivered to the inbox of your clients, not to the spam folder. It boosts the efficiency of your email campaigns and, consequently, increases ROI.
Read more: What is DMARC? The Top 5 Benefits of DMARC!
6. How to Implement DMARC with GlockApps
To create a DMARC record and get the DMARC reports, you can use the GlockApps DMARC Analytics.
The GlockApps DMARC Analytics will parse aggregate and forensic reports and present you the valuable data about your email traffic in a comprehensive and user-friendly format.
You can use DMARC Analytics for free with 10,000 messages every month in your account.
Start receiving DMARC data today!
Learn More About DMARC:
DMARC Report Analyzer- Improve Email Deliverability
Why Every Business Needs DMARC
How to Protect Sender Domain with DMARC: Using DMARC Enforcement
DMARC Adoption in 2023: What’s the Problem?