Strengthening DMARC Policies: A Crucial Defense Against North Korean Spearphishing Attacks
Estimated reading time: 5 minutes
Protect Your Email from Active Threats: FBI and Industry Leaders Stress the Importance of Proper DMARC Configuration
The FBI, U.S. Department of State, and NSA have issued a warning about North Korean cyber actors exploiting weak DMARC (Domain-based Message Authentication, Reporting, and Conformance) security policies to strengthen their phishing attacks. These fraudulent campaigns involve sending fake emails that look like they come from legitimate domains and trick recipients into sharing sensitive information.
As is known, DMARC is an important email security protocol that helps verify whether an email message genuinely originated from an organization’s domain. Properly configured DMARC policies can prevent malicious actors from sending spoofed emails that appear to come from trusted sources. However, North Korean actors, identified as the “Kimsuky” group, are taking advantage of misconfigured DMARC policies to send emails that appear to be legitimate. This tactic allows them to pose as credible journalists, academics, or experts to conduct social engineering and gather intelligence on geopolitical events and foreign policy strategies.
In a May 2nd, 2024 Cybersecurity Advisory (CSA) JCSA-20240502-001, the FBI, State Department, and NSA highlighted the urgent need for robust DMARC configurations to counteract North Korean spearphishing attacks. NSA Cybersecurity Director Dave Luber stated that spearphishing continues to be a mainstay of the DPRK cyber program, and this CSA provides new insights and mitigations to counter their tradecraft.
These phishing campaigns target experts in East Asian affairs and aim to gain access to private documents, research, and communications. The emails often contain realistic content and use compromised legitimate email accounts to enhance their authenticity.
Recognize Red Flag Indicators of Suspicious Emails
It is important to note that such letters can be recognized by the following key Red Flag Indications:
- Initial emails without malicious links followed by emails with malicious content, harmful links or documents;
- Emails that include genuine text from previous communications between victims and legitimate contacts;
- Poor English grammar and awkward sentence structure;
- Communications directed at individuals with direct or indirect knowledge of policy information, including U.S. and ROK government officials, high-clearance employees, and military personnel;
- Email addresses that look very similar to legitimate domains with subtle misspellings and addresses found in university directories or official websites;
- Request the recipient to click “Enable macros to view ” in the attached documents, a common tactic to deploy malicious software;
- Follow-up emails within 2-3 days if there is no response to the initial spearphishing email;
- Emails claiming to be from official sources but sent using unofficial email services, detectable through slightly incorrect email headers mimicking an organization’s domain.
Actions to Take Today to Protect Your Email from Malicious Activity
Security organizations recommend setting up proper configurations to mitigate malicious activity. Update the DMARC security policy for you or your organization to one of the two configurations below:
- Quarantine unauthorized emails;
- Reject unauthorized emails.
Monitoring email headers for inconsistencies in sender domains and reply addresses can also help identify suspicious emails.
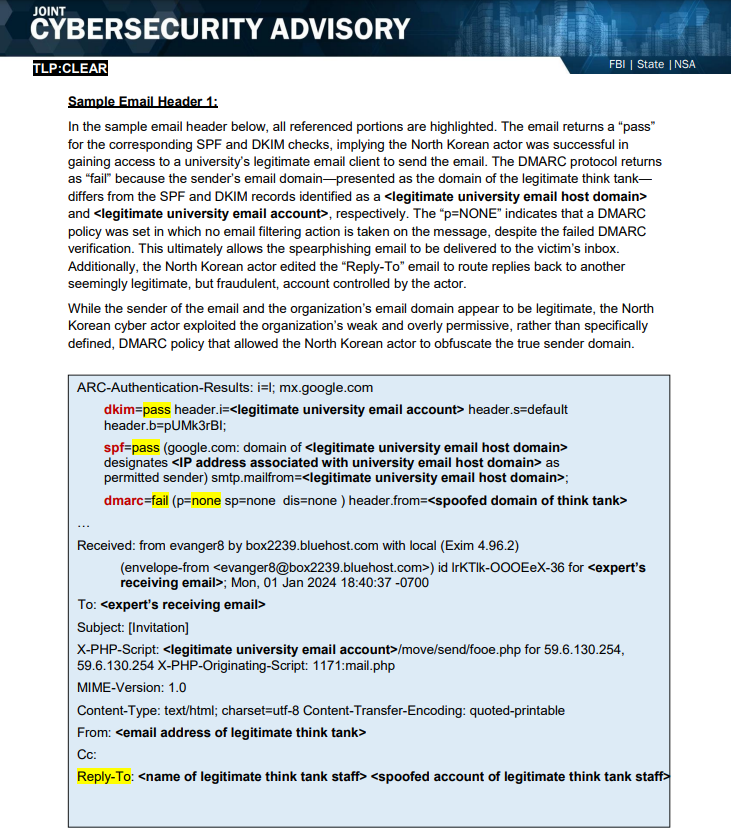
In the advisory, you can find detailed samples of such spearphishing emails, along with corresponding email headers demonstrating how North Korean actors exploit weak DMARC policies to obfuscate the true sender domain and successfully deliver malicious content to victims’ inboxes.
The report emphasizes that if you have fallen victim to one of these fraudulent campaigns, regardless of whether or not it resulted in compromise (especially if you are from one of the targeted sectors), please report the incident to www.ic3.gov with reference #KimsukyCSA, providing detailed information such as the sender’s email address and the content of that email.
Protect Your Brand from Cyber-Attacks with DMARC Analyzer
Deploying a DMARC protocol offers advantages regardless of a company’s scale. A DMARC record provides full domain control, regulates email flow, and protects against phishing and spoofing attempts. Plus, it improves email deliverability as it allows mailbox providers to verify your legitimacy as a sender when your emails are properly authenticated.
Use these simple steps to start with GlockApps DMARC monitoring and get valuable insights into your email traffic in a comprehensive and user-friendly way:
Add Your Domain: Access the DMARC Analytics tab, and then go to the “Add Domain” section. Enter your domain name and click Next. If you already have a DMARC record, consider using the one generated by GlockApps.
Select Your DMARC Policy: In the Configure DMARC tab, configure your DMARC policy based on the recommended settings provided in the Advisory – “Quarantine” or “Reject”.
Choose Alignment Mode in the Advanced Options tab:
- DKIM Alignment: Strict (matching domains) or Relaxed (different domains);
- SPF Alignment: Strict (matching domains) or Relaxed (different domains).
Generate DMARC Record and Publish in your DNS: After setting up, click Next to generate the DMARC record based on your selected settings. Copy the record, go to your domain’s DNS settings, and publish or update the record accordingly. Confirm the publication by clicking “I published the record”.
Review DMARC Compliance: It takes 1-2 days to collect data and generate DMARC reports after publishing the record. Check your DMARC compliance and view aggregate reports in the Domains Overview tab.
Using GlockApps DMARC Analyzer, you’ll receive detailed reports in an easy-to-understand format every 24 hours alerting you to any suspicious activity detected on your domain.
To Conclude
The advisory from the FBI, U.S. State Department, and NSA emphasizes that organizations are strongly encouraged to update their DMARC policies to mitigate phishing attacks. Proper configurations include setting the policy to “Quarantine” or “Reject” emails that fail authentication, where “Quarantine” would mean that mail servers should treat unauthenticated emails as potential spam, while “Reject” would tell the servers to block such emails completely.
Take action now to prevent a breach before it happens – our DMARC analyzer will be your reliable tool for better protection against spearphishing emails. Get free access to DMARC Analytics with 10,000 messages per month included in your account.