[Case Study] How We Stopped Spam from Our Domain with DMARC Analytics

After the adoption of DMARC, email marketing experts say that it is a must-have protocol for good email deliverability. Firstly, email messages passing DMARC email authentication are more likely to be delivered to the Inbox. Secondly, DMARC allows control of email delivery and protects the domain with a DMARC policy.
We didn’t think about DMARC until recently as we were simply sending emails the old-fashioned way. After hearing so much about it, I decided to Google it and came across the DMARC Analytics service from GlockApps and decided to try it as our company used email as the main channel of communication with our clients and subscribers, and email deliverability was our concern.
We subscribed to a plan that provided 1 million DMARC messages per month, published a DMARC record with the ‘none’ policy (a monitoring mode) following advice from Andrew at GlockApps chat support, and started waiting for reports.
The next day, we received the following message from GlockApps:
You've used over 95% of your DMARC capable messages limit. You have -7,783,712 out of 1,000,000 DMARC points. We charge an additional $10 for every 1,000,000 of the over-quota volume.
7 million emails?!! What the hell?!! We’re used to sending no more than 800k emails per month. We logged in to our GlockApps dashboard to analyze DMARC reports and see who could have sent such a huge number of emails from our domain in just one day. We saw a lot of IP addresses that were unfamiliar to us. The weird thing was that all of the IP addresses were ‘green’ which meant all of them were authorized to send emails on behalf of our domain.
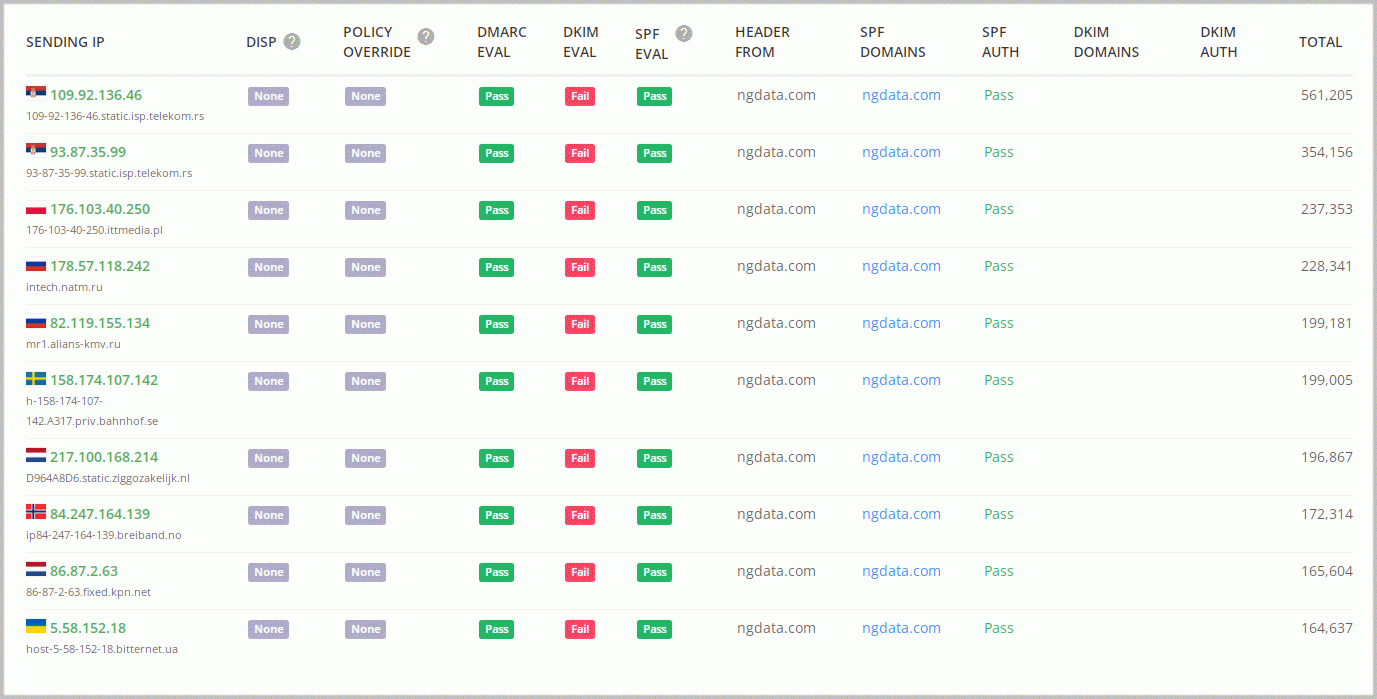
The first thought was that GlockApps had a glitch. Then we decided to check the SPF record for our domain. In DNS, everything looked good.
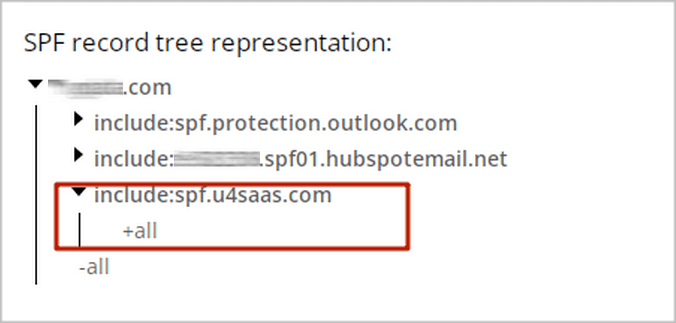
But after verifying the record with the GlockApps SPF Validator, we found where the issue was:
One of the ‘include’ mechanisms contained ‘+all’. Huge red flag! It meant that our SPF record authorized ANY IP address to send emails from our domain. With the ‘none’ policy, it opened the doors to everyone. And spammers didn’t miss that opportunity.
We fixed the SPF record and the volume of emails sent from our domain went back to normal.
I’m pleased that GlockApps alerted us about the exceeded quota and additional fee in a timely fashion. Otherwise, we would have had to pay an additional $2,300 for 233 million unwanted emails that would have been sent that month.
Thanks to the GlockApps DMARC Analytics service, we found out about a big issue with our DNS record, which was responsible for email deliverability, and corrected it before it affected our domain reputation.



