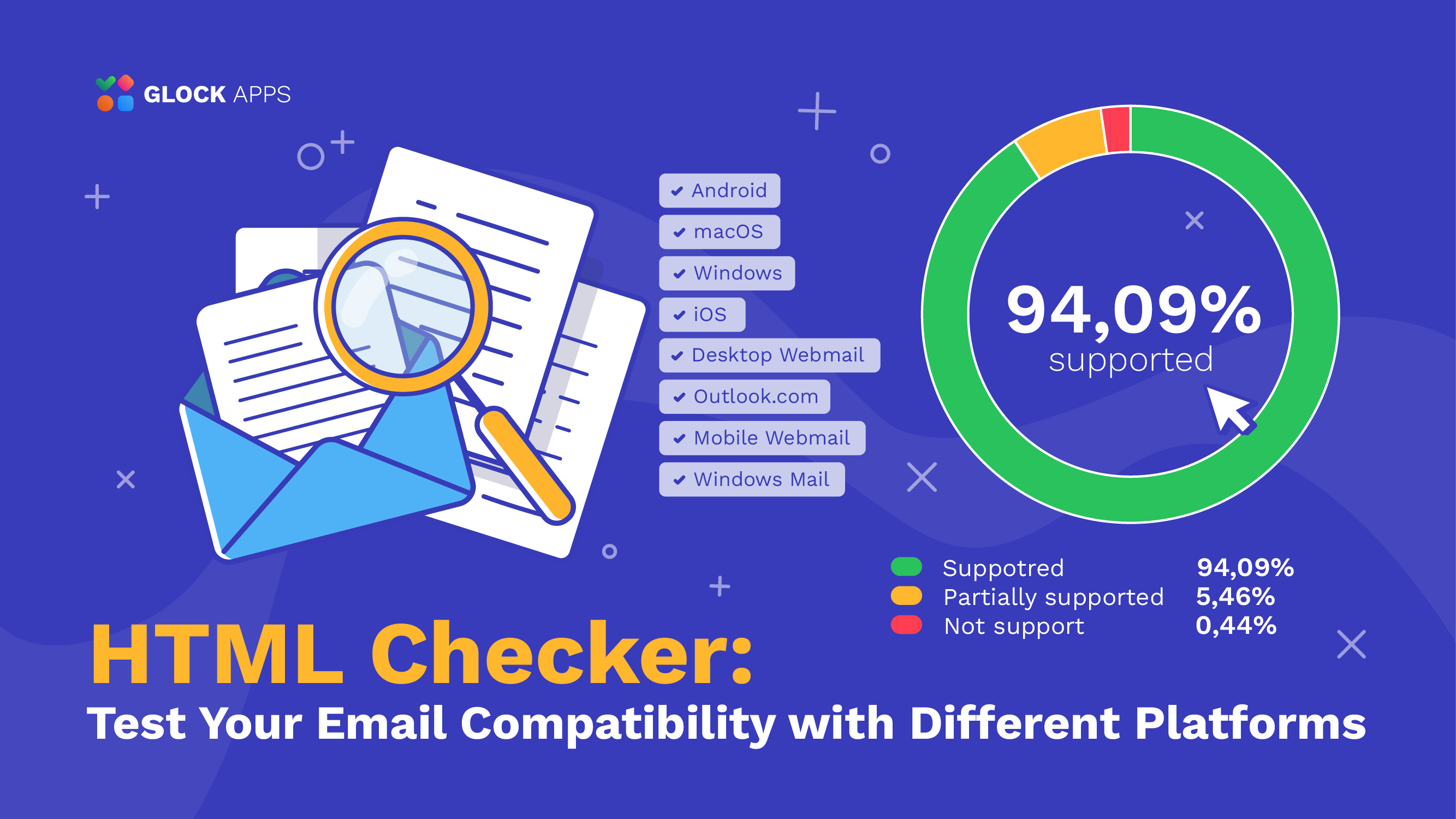
The Role of Follow-Up Emails in Email Marketing Strategy: Effective Templates for Different Cases
Follow-up emails are like a kind reminder in the inbox that keeps the conversation going. They play an important role in building relationships, offering value, and pushing people to take action. That’s why you should include them in your email marketing strategy to show your recipients that you have them in mind and are always ready to engage.